In the wild world of blockchain development, where memes meet million-dollar trades, even the smallest coding slip can turn a smooth swap into a slippery slope. Welcome to Advent of Bugs #4, a holiday-season reminder from the Accretion team on why you shouldn't treat bananas like oranges – or base currencies like quote assets – in your Solana smart contracts.
If you've ever tinkered with decentralized exchanges (DEXes), you know an Automated Market Maker (AMM) is the engine behind those lightning-fast token swaps on Solana. But as this tweet highlights, a sneaky bug in the swap logic could let trades slip through with unchecked slippage, potentially leaving traders with fewer tokens than expected. Let's break it down, banana-style.
The Bug: When u64 Hides a Fruit Salad
The code in question handles four common AMM swap scenarios:
- Buy ExactIn: You specify the exact input amount of quote tokens (say, SOL) and get a variable output of base tokens (your favorite meme coin).
- Buy ExactOut: You want a specific output amount and pay whatever input is needed.
- Sell ExactIn: Input base tokens for variable quote output.
- Sell ExactOut: Fixed quote output, variable base input.
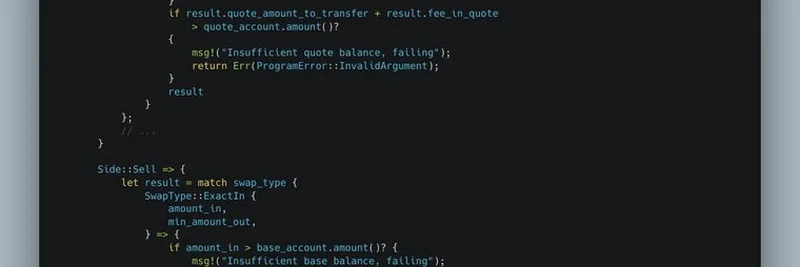
At first glance, the buy paths look solid – clean calculations, proper error handling for insufficient balances or invalid data. But zoom in on the Sell ExactIn path, and you'll spot the rot: the slippage check was comparing base amounts against quote amounts.
Think of it like this: Your recipe calls for 5 bananas, but you're checking if you have 5 oranges instead. Both are just fruits (or in code terms, both are u64 integers), so the comparison doesn't throw an error. The check passes when it shouldn't, allowing a swap to execute with way more slippage than intended. Ouch – that's a recipe for trader regret.
Here's a peek at the problematic snippet from the tweet's first image:
The second image dives deeper into the sell-side fallout:
No compile-time warnings, no runtime crashes – just silent failure. This gremlin survived three audits. Why? Rust's type aliases let u64 masquerade as different units without batting an eye.
Why It Matters in Meme Token Land
Meme tokens thrive on Solana's speed and low fees, powering viral pumps and community-driven DEXes like Raydium or Orca. But when swap bugs like this lurk, they erode trust. Imagine a hot new dog-themed token launch: Traders front-run with big sells, slippage goes unchecked, and suddenly the meme's moonshot turns into a rug-pull vibe. For blockchain devs building the next PEPE or WIF, ignoring unit safety isn't just sloppy – it's a liquidity leak waiting to happen.
The Fix: Wrap It Up with Newtypes
Accretion's pro tip? Ditch plain u64 aliases for newtype structs in Rust. These are simple wrappers that enforce type safety at compile time. Something like:
rust
#[derive(Debug, PartialEq)]
struct BaseAmount(u64);
#[derive(Debug, PartialEq)]
struct QuoteAmount(u64);
impl BaseAmount {
fn to_u64(&self) -> u64 { self.0 }
// Add ops like add, mul for safe arithmetic
}
Now, trying to compare BaseAmount(5) with QuoteAmount(5)? Compiler says no – "mismatched types." Bananas stay bananas, oranges stay oranges. It's a small refactor that pays off big in audit-proof code.
This isn't just theory; it's battle-tested advice from Solana security pros. If you're auditing or launching an AMM, check out Accretion's services – they're hiring top auditors and spotting bugs before they bite.
Wrapping Up: Fruitful Lessons for Solana Devs
Advent of Bugs is a yearly ritual that's equal parts festive and frightening, reminding us that even pros mix up units. As meme tokens evolve from jokes to juggernauts, robust code keeps the community thriving. Got a similar war story? Drop it in the comments – let's audit the future together.
Stay safe out there, degens. And remember: In smart contracts, precision isn't optional – it's the peel between profit and pulp.