The DeFi space never sleeps, and neither do the hackers. Recently, Astera Finance, a lending protocol built on the Linea blockchain and focused on providing instant liquidity and yield for stablecoins like USDT, fell victim to a clever exploit. What started as reports of an oracle pricing USDT at a whopping $154 turned out to be something more intricate: a manipulation of the liquidity index. Let's break it down step by step, drawing from insights shared by blockchain security firm Phalcon in their recent thread.
First off, a quick primer for those new to DeFi. Astera Finance is essentially a fork of Aave, a popular lending platform where users can deposit assets to earn interest or borrow against their collateral. In these systems, the "AToken" represents your deposited assets and accrues interest over time through something called the liquidity index—a multiplier that reflects the accumulated interest in the pool.
Security researcher Weilin Li kicked off the discussion by calling it a "textbook oracle misconfiguration." An oracle, by the way, is a service that feeds real-world price data into smart contracts. According to Li, the attacker pulled 10 ETH from Tornado Cash (a privacy mixer for transactions), bridged it to Linea about a week prior, deposited 6,000 USDT—which the faulty oracle valued at around $900,000—and then borrowed about $573,000 against that inflated collateral. The attacker's health factor (a measure of how safe their loan is from liquidation) hilariously remained at 1.45 even after the heist.
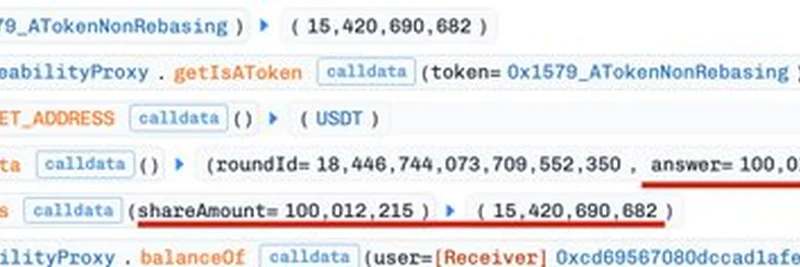
But Phalcon stepped in to clarify: this wasn't about the oracle at all. The underlying USDT price from the oracle stayed steady at about $1. The real trick was in inflating the liquidity index from 1.001 to 154 through a barrage of flashloan transactions. Flashloans are uncollateralized loans that must be repaid in the same transaction—perfect for short-term manipulations without risking your own capital.
As shown in Phalcon's analysis above, the attacker used repeated borrow-and-repay cycles to rack up fees and distort the index. Unlike typical one-shot attacks on empty pools in Aave forks, this one took multiple transactions because the market had existing liquidity.
Here's how it unfolded:
Step 1: Setting Up Positions
The primary attacker address (0x61EA1C91d7aE9782223384fAFe3ad81fFb8E0b45) created positions by depositing assets into the pool. Check out the transaction here: Deposit TX.
Step 2: Inflating the Liquidity Index
A secondary address (0x9520C9040338bE61005590cC1BD15caa10a6613c) then hammered the pool with around 100 flashloan operations. This gradually pumped the liquidity index sky-high. The first inflation transaction: First Inflation TX. And the final one that sealed the deal: Final Inflation TX.
Step 3: Draining the Pool
With the AToken price now artificially bloated (you can view the AToken contract for USDT here: AToken USDT), the main attacker borrowed heavily against their deposits and siphoned funds from the lending pool.
Astera Finance quickly responded by pausing their Core Pool and Mini Pools upon detecting the breach. Phalcon noted that we're still awaiting the official post-mortem report for full details, but this incident highlights a key vulnerability in Aave-forked protocols: insufficient protections against iterative manipulations in non-empty markets.
For blockchain practitioners and meme token enthusiasts alike, this serves as a reminder of the risks in DeFi lending. While meme tokens often thrive on hype and community, underlying infrastructure like lending pools can be prime targets. If you're building or investing in similar projects, consider adding safeguards like rate limits on flashloans or better liquidity monitoring to prevent such index inflations.
Stay vigilant out there—DeFi is innovative, but it's also a playground for sophisticated attacks. For more on blockchain security and the latest in meme token news, keep following Meme Insider.