A massive security breach shook the DeFi world today, with Balancer and several of its forked projects falling victim to a clever exploit. According to a detailed analysis from BlockSec's Phalcon team on X (formerly Twitter), attackers drained over $120 million across various blockchains. This isn't just another hack—it's a masterclass in exploiting mathematical precision in decentralized finance protocols.
Let's break it down step by step, keeping things straightforward. Balancer is a popular automated market maker (AMM) that lets users create liquidity pools with customizable weights. It's known for its flexibility, but that complexity can sometimes open doors to vulnerabilities, especially in how it calculates prices and invariants—the core math that keeps pools balanced.
The Root Cause: Invariant Manipulation and Rounding Errors
The exploit revolves around messing with the "invariant" in Balancer's stable pools. Think of the invariant as a constant value that represents the total "worth" of the pool based on Curve's StableSwap model. It's used to calculate the price of Balancer Pool Tokens (BPT), which are like shares in the pool. The formula is simple: BPT price = Invariant (D) / Total Supply.
Attackers found a way to artificially deflate this BPT price through a series of swaps, then buy back in at the lower price for profit. This was done via a single "batch swap," which bundles multiple trades together. Here's how it unfolded, using an example transaction on Arbitrum:
Setting the Stage: The hacker starts by swapping BPT for underlying assets, tweaking the balance of one token (in this case, cbETH) to land exactly on a "rounding boundary." They aim for a tiny amount, like 9 units, which sets up precision issues in the next steps.
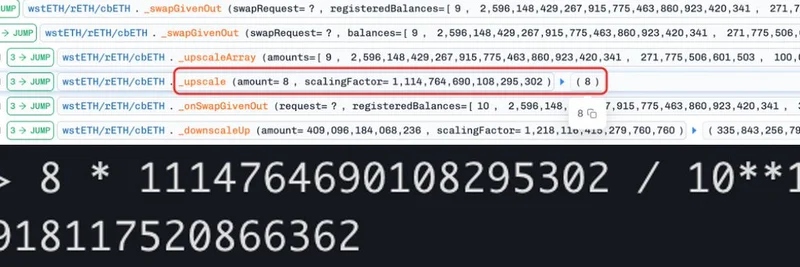
The Key Manipulation: Next, they swap between another asset (wstETH) and cbETH with a carefully chosen amount—8 units. Because Balancer scales token amounts with rounding down (to handle decimals), the calculated change in one token (Δx) ends up slightly smaller than it should be. This leads to an underestimated change in the other token (Δy), shrinking the overall invariant. Boom—the BPT price drops.
As seen in the code logs above, the scaling factor causes the amount to round down from about 8.918 to 8, creating that distortion.
- Cashing Out: Finally, the attacker reverses the swaps, putting assets back into the pool and minting BPT at the now-deflated price. They restore the balances but walk away with extra tokens, which they can sell for profit.
This precision play exploits how smart contracts handle big numbers and decimals. In blockchain terms, tokens often use 18 decimal places, so even tiny rounding errors can be amplified in large pools.
The Impact: Losses Across Chains
The attack didn't stop at one network. Phalcon's earlier alert highlighted hits on multiple chains:
- Ethereum: $70 million from Balancer
- Base: $3.9 million from Balancer
- Polygon: $117,000 from Balancer
- Sonic: $3.4 million from Beethoven X (a fork)
- Arbitrum: $5.9 million from Balancer
- Optimism: $283,000 from Beethoven X
Forked projects like Beethoven X were especially vulnerable since they inherit Balancer's code. If you're in DeFi, this is a reminder to check your exposures—withdraw from affected pools if needed and stay updated via official channels like Balancer's X account.
Why This Matters for Meme Token Enthusiasts
While Balancer isn't directly about meme coins, many meme projects build on DeFi infrastructure like this. Liquidity pools are the backbone of trading tokens on platforms like Uniswap or Raydium, and similar vulnerabilities could trickle down. If you're launching or trading memes, understanding these risks helps you spot safer protocols. Plus, exploits like this often lead to market dips, creating buying opportunities—or warnings to steer clear.
Lessons Learned and Next Steps
DeFi's permissionless nature is a double-edged sword: innovative but risky. Audits help, but as this shows, even well-vetted code can have edge cases. Projects should consider adding more robust rounding safeguards or emergency pauses. For users, diversify, use hardware wallets, and follow security firms like BlockSec for real-time alerts.
This exploit highlights the ongoing cat-and-mouse game in crypto security. Stay vigilant, and remember: in DeFi, knowledge is your best defense. If you've got thoughts on this hack or similar stories, drop them in the comments below!