Hey there, crypto enthusiasts! If you're knee-deep in the world of decentralized finance (DeFi) or even just dipping your toes into meme tokens, you've probably heard about liquidity pools and how they keep the trading wheels turning. But what happens when a clever hacker finds a way to game the system? That's exactly what went down with Balancer and some of its forked projects, leading to a whopping $120 million in losses across multiple blockchains. Let's break it down step by step, based on the alert from security pros at BlockSec's Phalcon.
The Initial Alert: A Multi-Chain Meltdown
It all started with a urgent heads-up from Phalcon on X (formerly Twitter). They flagged that Balancer, a popular automated market maker (AMM) protocol for creating customizable liquidity pools, along with several projects that forked its code, had been hit hard. Forks are essentially copies or variations of the original code, like Beethoven X on Optimism or BEETS on Sonic.
The damages? Pretty staggering:
- Ethereum: $70 million from Balancer
- Base: $3.9 million from Balancer
- Polygon: $117,000 from Balancer
- Sonic: $3.4 million from BEETS
- Arbitrum: $5.9 million from Balancer
- Optimism: $283,000 from Beethoven X
Phalcon urged any projects using similar code to stay vigilant and monitor their systems closely. You can check out the original alert here.
This kind of attack isn't just a blip—it's a reminder of the vulnerabilities in DeFi protocols, especially for meme token launches that often rely on these pools for liquidity. If your favorite dog-themed coin is swimming in a Balancer-style pool, events like this could ripple out and affect prices or trading.
Diving into the Exploit: How It Happened
Phalcon's follow-up post dissected the attack, calling it a "highly sophisticated exploit." The root cause? Something called invariant manipulation. In simple terms, an invariant in protocols like Balancer (which draws from Curve's StableSwap model) is a mathematical constant that represents the total value in the pool. It's used to calculate prices and ensure trades are fair.
Hackers messed with this invariant to artificially deflate the price of Balancer Pool Tokens (BPTs)—the tokens that represent your share in the pool. By doing so, they could buy BPTs on the cheap and then swap back for profits.
To illustrate, let's look at an example attack transaction on Arbitrum. The exploit unfolded in three slick phases during a single "batch swap" (a way to execute multiple trades at once):
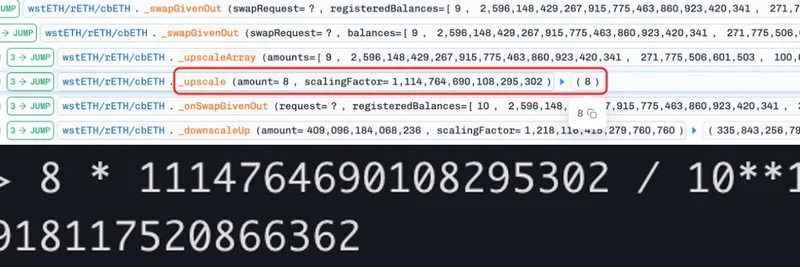
Setup the Trap: The attacker swapped BPT for underlying assets, tweaking the balance of one token (cbETH, a wrapped version of Coinbase's staked ETH) to hit a precise "rounding boundary." Basically, they set one token's amount to 9, priming the pool for a calculation glitch.
Trigger the Manipulation: Next, they swapped between another token (wstETH, wrapped staked ETH) and cbETH with a carefully chosen amount of 8. Due to how the protocol handles scaling and rounding down (to avoid precision issues in blockchain math), the computed change in one token (Δx) ended up smaller than it should be—dropping from about 8.918 to just 8. This underestimated the output (Δy), shrinking the invariant and tanking the BPT price.
Cash Out: Finally, the attacker reversed the swaps, putting assets back into the pool and snagging BPT at the deflated price. Boom—profits locked in while the pool's balances normalized.
Here's a visual from Phalcon's analysis showing the code in action:
For the tech-savvy, the key was exploiting rounding errors in functions like upscale and downscale, which adjust token amounts based on decimals. The attacker used this to create a tiny discrepancy that snowballed into millions.
You can dive deeper into the full breakdown in Phalcon's post here.
Why This Matters for Meme Tokens and DeFi
Balancer isn't just for blue-chip assets; it's a go-to for creative pools, including those powering meme tokens. If a project forks Balancer without patching these kinds of issues, it could expose liquidity providers (LPs) to similar risks. Meme coins, with their viral hype and rapid launches, often use these protocols to bootstrap trading—meaning an exploit could wipe out community funds or crash prices overnight.
This attack underscores the need for robust audits and real-time monitoring in blockchain. Tools like Phalcon help detect these threats early, but as DeFi evolves, so do the hackers. If you're building or investing in meme tokens, keep an eye on the underlying tech stack.
Lessons Learned and Next Steps
In the wake of this, Balancer and affected forks are likely scrambling to patch and recover. For the broader community:
- Audit Everything: Even forked code needs fresh eyes.
- Monitor Actively: Use services like Phalcon for threat detection.
- Diversify Risks: Don't put all your eggs in one pool—spread liquidity across protocols.
Stay safe out there, and remember: in crypto, knowledge is your best shield. If you've got thoughts on this exploit or similar stories, drop them in the comments below!