Hey there, crypto enthusiasts! If you’ve been keeping an eye on the meme token scene, you’ve probably heard about the latest drama involving Bankroll Status. A series of attacks has rocked this project, leading to a staggering $400,000 in losses since September 2024. Let’s break it down in a way that’s easy to digest, even if you’re new to the blockchain world.
What Happened?
According to a recent tweet from BlockSec Phalcon, a blockchain security firm, attackers have been exploiting a flaw in Bankroll Status’ smart contract. The vulnerability lies in the distribute() function, which handles how rewards are shared among token holders. Here’s the catch: this function updates the global profitPerShare_ only after syncing a user’s _updatedPayouts during buy or sell operations. This sequencing issue creates a loophole that clever attackers have been using to their advantage.
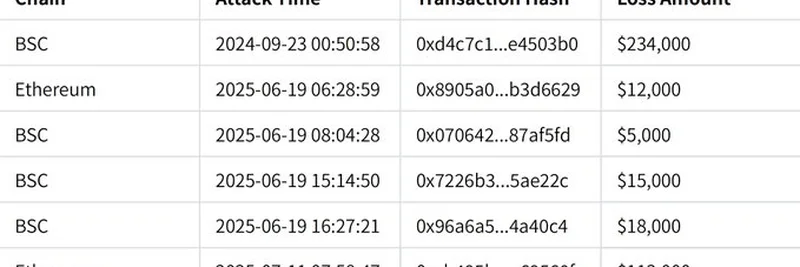
The attacks have hit both Ethereum and BSC (Binance Smart Chain), with the latest strike on July 11, 2025, resulting in a $113,000 loss. Check out the table below for a rundown of the incidents:
- BSC: $234,000 (Sept 23, 2024)
- Ethereum: $12,000 (June 19, 2025)
- BSC: $5,000 (June 19, 2025)
- BSC: $15,000 (June 19, 2025)
- BSC: $18,000 (June 19, 2025)
- Ethereum: $113,000 (July 11, 2025)
That’s a total of $400,000 drained from the project, and sadly, the Bankroll Status team hasn’t responded to attempts to reach out.
How Did the Attack Work?
So, how are these attackers pulling this off? It’s all about timing and manipulation. Here’s a simple explanation:
- Big Buys: An attacker buys a large amount of tokens using multiple staking contracts.
- Quick Sell: They immediately sell those tokens.
- Reward Grab: Because of the flaw in the
distribute()function, the attacker claims more dividends than they should before the system catches up.
In the most recent attack, the culprit even donated ETH to the pool first to ensure there were enough rewards to drain. This move was front-run by an address called c0ffeebabe.eth, adding another layer of complexity. You can dive into the transaction details here if you’re curious!
Why This Matters for Meme Token Fans
Meme tokens like Bankroll Status often ride the wave of community hype, but this incident is a stark reminder that security can’t be an afterthought. Smart contracts—the self-executing code that powers these tokens—need to be rock-solid. A single vulnerability can lead to massive losses, shaking investor confidence and potentially tanking a project.
This isn’t the first time we’ve seen such exploits. Projects like Four.Meme have faced similar issues, losing significant funds due to launch function flaws. It’s a wake-up call for developers to audit their code thoroughly and for investors to do their homework before jumping in.
What Can Be Done?
If you’re a blockchain practitioner or just a curious meme token enthusiast, here are a few takeaways:
- Audits Are Key: Projects should use tools like BlockSec Phalcon to catch vulnerabilities early.
- Stay Informed: Follow security alerts on platforms like X to stay ahead of potential risks.
- Diversify: Don’t put all your eggs in one basket—spread your investments to minimize losses.
For now, Bankroll Status is in hot water, and the lack of response from the team isn’t helping. We’ll keep you posted on any updates here at Meme Insider. Got thoughts on this exploit? Drop them in the comments—we’d love to hear from you!