Hey there, crypto enthusiasts and blockchain developers! If you’ve ever been tempted by a promising job offer on LinkedIn that comes with a GitHub repo to test your skills, this article is a must-read. A recent tweet from sudo rm -rf --no-preserve-root / on July 4, 2025, sheds light on a sneaky scam that’s been draining crypto wallets. Let’s dive into the details and learn how to stay safe!
The Hidden Danger in Next.js Repos
Imagine this: you get a message from someone claiming to offer a legit job opportunity. They send you a GitHub repository with a simple Next.js task to complete. You clone it, run it, and within minutes, your hot wallets are empty. Sounds like a nightmare, right? According to the tweet, this is a real attack pattern that the SEAL 911 team has seen repeatedly.
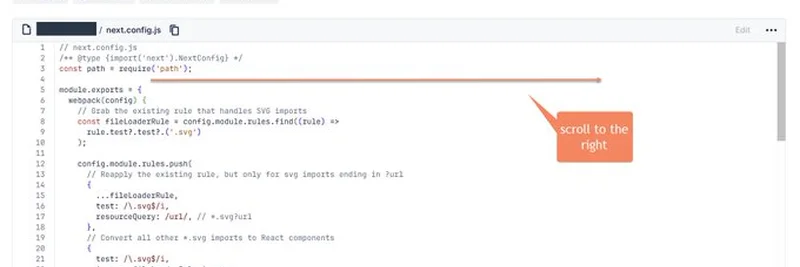
The catch? The malicious code is hidden in the next.config.js file—a key configuration file for Next.js projects. This file might look harmless at first glance, but the danger lurks far to the right, padded with extra spaces. The tweet includes a screenshot showing how scrolling horizontally reveals the hidden payload. Check out the image above to see it for yourself!
How the Scam Works
Here’s the breakdown: scammers disguise their repos as legitimate coding tasks. Once you run the code, it executes a payload that compromises your device. For crypto users, this often means accessing and draining your hot wallets—those connected to the internet for quick transactions. The tweet warns that even a quick LinkedIn profile check won’t always spot the red flags.
Safety Tips to Avoid Falling Victim
Don’t worry—there are ways to protect yourself! Here are some practical tips from the thread and beyond:
- Never Run Random Code: Seriously, resist the urge to execute code from unknown sources. It’s like opening a random email attachment—better safe than sorry!
- Scroll and Inspect: Always scroll horizontally through config files like
next.config.js. Malicious code can be tucked away where you least expect it. - Use a Virtual Machine (VM): If you must test code, run it in a VM. This isolates the code from your main system, minimizing risk. The original poster even suggested this in a follow-up reply.
- Verify the Source: Double-check the sender’s credentials and the repo’s history. If it looks fishy, steer clear.
Why This Matters for Blockchain Practitioners
As someone working in the blockchain space, you’re a prime target for these scams. Your crypto wallets hold valuable assets, and scammers know it. This incident highlights the importance of cybersecurity in the decentralized world. By staying vigilant, you can protect your funds and keep building awesome projects.
Community Reactions
The X thread sparked some interesting responses. Users like versteckt emphasized avoiding any code from suspicious sources, while GrumpyTechChad plans to cover this in an educational piece. Others, like 0b501e7e, noted that non-security folks might not use VMs, underscoring the need for awareness.
Stay Informed with Meme Insider
At Meme Insider, we’re all about keeping you updated on the latest in blockchain and meme token news. This scam is a reminder to stay cautious, especially with the rise of meme coins and decentralized finance (DeFi). Bookmark our site and dive into our knowledge base to level up your skills and stay ahead of the curve!
Have you encountered similar scams? Drop your thoughts in the comments below—we’d love to hear from you!