Unmasking the Solana PumpFun Bot GitHub Scam
Hey there, crypto enthusiasts! If you’ve been keeping an eye on the blockchain world, you might have come across an alarming incident reported by the SlowMist team on July 4, 2025. A seemingly legit GitHub project called solana-pumpfun-bot turned out to be a clever trap that stole crypto assets from unsuspecting users. Let’s dive into what happened and how you can stay safe.
How the Scam Unfolded
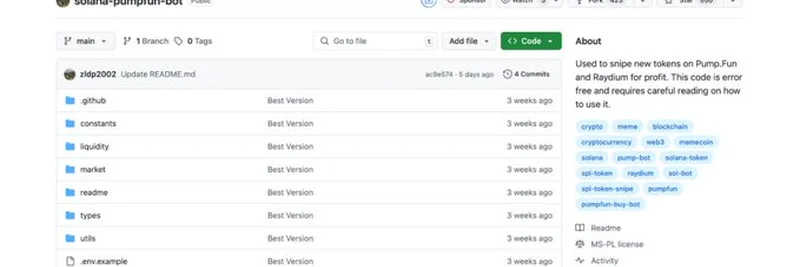
On July 2, 2025, a victim reached out to SlowMist after losing their crypto holdings. The culprit? They had downloaded and run the solana-pumpfun-bot project from GitHub, thinking it was a handy tool for trading on the Solana blockchain. This Node.js-based project promised to snipe new tokens on PumpFun, a popular platform, but it came with a nasty surprise.
The project looked legit at first glance. It had a decent number of stars and forks, which are signs of popularity on GitHub. But here’s the catch: the code was packed with malicious dependencies. One sneaky package, crypto-layout-utils, was designed to scan for private keys and wallet data, then send that info to a server controlled by the attacker (githubshadow.xyz). Yikes!
The Deceptive Tactics
So, how did this scam pull the wool over users’ eyes? The attackers used a mix of social engineering and technical tricks. They artificially boosted the project’s credibility by creating multiple GitHub accounts to fork the repo and add stars. This made it look like a trusted community project. Plus, the malicious package was hosted on a custom URL instead of the official NPM registry, making it harder to spot.
SlowMist’s investigation revealed that the attacker even swapped out the NPM source link in the package-lock.json file to point to a shady download (https://github.com/sjaduwhv/testing-dev-log/releases/download/1.3.1/crypto-layout-utils-1.3.1.tgz). Once installed, the obfuscated code went to work, silently exfiltrating sensitive data.
Who’s at Risk?
This scam targeted anyone interested in Solana-based trading bots, especially those new to the space. The promise of easy profits from sniping tokens on PumpFun lured users in, but it came at a steep cost. The attackers also used other malicious packages like bs58-encrypt-utils and created a network of fake repos to spread the malware further.
Staying Safe in the Crypto World
Don’t worry—there are ways to protect yourself! Here are some practical tips:
- Vet GitHub Projects: Always check the repo’s history, contributors, and update frequency. A sudden spike in stars or forks can be a red flag.
- Use Isolated Environments: Test new projects in a sandbox or virtual machine to keep your real wallet data safe.
- Avoid Sharing Private Keys: Never run code that asks for your private keys or wallet access unless you trust the source 100%.
- Keep Software Updated: Regularly update your tools and dependencies to avoid vulnerabilities.
SlowMist also shared a list of malicious repos and packages to watch out for, so you can steer clear of them. Check their full report on Medium for more details.
Why This Matters for Meme Token Fans
At Meme Insider, we’re all about helping you navigate the wild world of meme tokens and blockchain tech. Scams like this remind us that even exciting tools can hide dangers. Whether you’re trading Solana-based meme coins or exploring new projects, staying informed is your best defense. We’re here to break down the latest news and build a knowledge base to empower you!
Final Thoughts
The Solana PumpFun Bot scam is a wake-up call for the crypto community. It shows how attackers can exploit trusted platforms like GitHub to target enthusiasts. By staying cautious and following security best practices, you can enjoy the blockchain space without falling into these traps. Got questions or tips of your own? Drop them in the comments—we’d love to hear from you!