Hey there, blockchain enthusiasts! If you're deep into meme tokens or just keeping an eye on the wild world of DeFi, you've got to stay vigilant about security. Recently, the folks at Phalcon—a top-notch blockchain security monitoring platform built by BlockSec—dropped an alert that's got everyone talking. They spotted a clever attack on an unknown smart contract on the Binance Smart Chain (BSC), resulting in a hefty loss of around $85,000. Let's break it down in simple terms and see what we can learn, especially for those building or investing in meme token projects.
What Happened in the Attack?
The attacker pulled off two sneaky transactions that exploited weaknesses in the contract's design. BSC, for the uninitiated, is a popular blockchain that's compatible with Ethereum but offers faster and cheaper transactions—making it a hotspot for meme tokens and DeFi apps. In this case, the hacker used something called EIP-7702, which is an Ethereum Improvement Proposal that allows accounts to temporarily delegate execution to another contract's code. Think of it as a way to "borrow" functionality on the fly, often used in advanced maneuvers like flash loans.
Here, the attacker applied EIP-7702 to their own address during a flash loan callback. Flash loans are instant, uncollateralized loans that must be repaid in the same transaction—super useful for arbitrage but also a favorite tool for exploits. By doing this, they manipulated prices, staked assets, and then quickly unstaked to pocket the profits. The whole thing hinged on bypassing the contract's built-in protections.
Phalcon shared the details in their tweet, including the attack transactions. The first one is linked here, and it shows how the hacker executed the stake and unstake in rapid succession.
The Three Key Vulnerabilities Exposed
Phalcon highlighted three main flaws that made this attack possible. Let's unpack them one by one, with easy explanations so even if you're new to smart contracts, you can follow along.
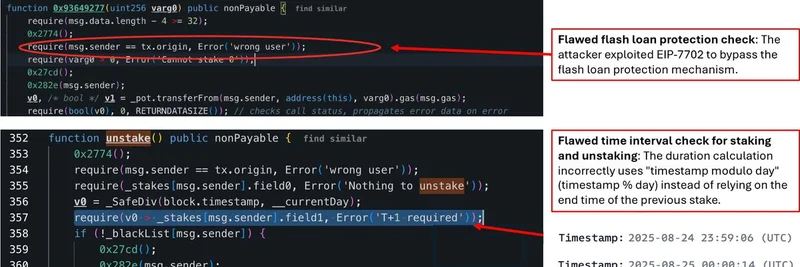
Flawed Flash Loan Protection Check: The contract had a mechanism to prevent abuse from flash loans, but it wasn't airtight. The attacker used EIP-7702 to delegate the callback, essentially tricking the contract into thinking everything was legit. This bypass let them manipulate the system without triggering the safeguards. Lesson for meme token devs: Always test your protections against the latest EIPs and delegation tricks.
Dependency on Spot Prices: The contract relied on current market prices (spot prices) for calculations, which can be easily manipulated in low-liquidity environments—like many meme token pools. The hacker skewed these prices during the flash loan to create an artificial profit opportunity.
Flawed Time Interval Check for Staking and Unstaking: This one's a doozy. The contract used a "timestamp modulo day" calculation (basically, timestamp % day) to check durations, instead of tracking the actual end time from the previous stake. This meant the hacker could stake and unstake almost immediately without waiting the required period, as long as they timed it across a day boundary. It's a classic example of why block timestamps aren't always reliable for time-sensitive logic in smart contracts.
These issues aren't unique to this contract; they've popped up in various DeFi and meme token projects. If you're launching a meme coin with staking features, double-check your time locks and price oracles to avoid similar pitfalls.
Why This Matters for Meme Tokens
Meme tokens often launch quickly with hype-driven mechanics like staking rewards or liquidity pools, but security can take a backseat. This BSC incident is a stark reminder that even "unknown" contracts can hold significant value and attract sophisticated attackers. With losses hitting $85K, it's not chump change—especially in the volatile meme space where community trust is everything.
At Meme Insider, we're all about arming you with the knowledge to navigate this ecosystem safely. Incidents like this underscore the need for audits from reputable firms like BlockSec and ongoing monitoring with tools like Phalcon. If you're a dev, consider integrating better oracle solutions (like Chainlink) for prices and more robust time checks.
Staying Safe in the Meme Token World
To wrap up, keep an eye on alerts from sources like Phalcon and always verify contract interactions. If you've interacted with suspicious contracts on BSC, revoke approvals ASAP using tools like Revoke.cash. And for the latest on meme token tech and security, stick with us at meme-insider.com—we've got your back.
What do you think? Have you seen similar exploits in meme projects? Drop your thoughts in the comments below!