As a former editor at CoinDesk now diving deep into the wild world of meme tokens at Meme Insider, I've seen my share of crypto mishaps. But the recent Bunni exploit really drives home a point made in this tweet by @0xngmi: writing smart contracts is brutal. Bunni, a shapeshifting DEX built on Uniswap v4 that aims to boost liquidity provider profits, suffered an $8.4 million hack due to a seemingly innocent rounding error. Let's break it down in simple terms, explore what went wrong, and discuss what it means for the broader DeFi and meme token ecosystem.
What Happened in the Bunni Exploit?
Bunni announced the exploit in their update thread, where they shared a detailed post-mortem. The attack hit two pools: weETH/ETH on Unichain and USDC/USDT on Ethereum. The hacker walked away with millions by manipulating the pool's liquidity perception through clever use of flashloans, tiny withdrawals, and sandwich attacks.
Here's the step-by-step playbook the attacker used, based on the official post-mortem:
Flashloan and Price Manipulation: The attacker borrowed a massive amount (like 3 million USDT) via a flashloan and swapped it into the pool, pushing the price way up. This left the active balance—the part of the pool used for swaps—super low, like down to just 28 wei in USDC.
Exploiting Tiny Withdrawals: Then came the sneaky part. The hacker made 44 super small withdrawals. Each one triggered a rounding error that chipped away at the pool's perceived liquidity far more than it should have. This dropped the total liquidity by about 84%, making the pool think it had way less assets than it actually did.
Sandwich Attack for Profit: With the liquidity artificially low, the attacker did a big swap that caused massive price slippage in their favor. They followed it up with another swap to cash out, repaid the flashloan, and pocketed the profits—around 1.33 million USDC and 1 million USDT.
Interestingly, the largest Bunni pool (USDC/USD₮0 on Unichain) dodged the bullet because there wasn't enough flashloan liquidity available to pull off the initial step.
The Root Cause: A Tricky Rounding Error
At the heart of this mess was a rounding decision in Bunni's smart contract code. In DeFi, rounding errors happen because we're dealing with integers (whole numbers) in smart contracts, and division often leaves remainders. Developers have to choose whether to round up or down, and that choice can make or break security.
In Bunni's withdraw() function, the code rounded in a way that was meant to favor the pool—making liquidity seem slightly lower to increase price impact during swaps, which benefits liquidity providers (LPs). But this backfired when combined with multiple operations.
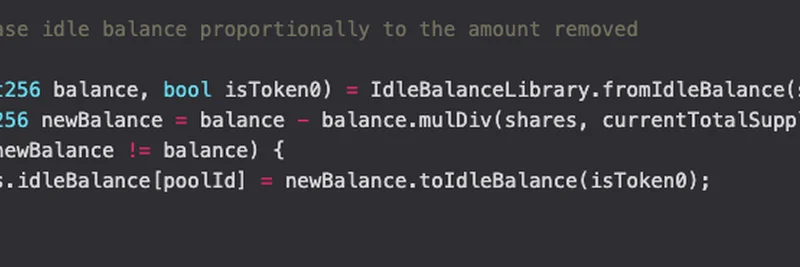
Here's the problematic code snippet from the post-mortem:
The line newBalance = balance - balance.mulDiv(shares, currentTotalSupply) uses a rounding-down multiplication-division (mulDiv), which effectively rounds the subtracted amount down. This means the new idle balance rounds up, and the active balance (what's left for swaps) rounds down. Alone, it seems safe. But repeat it with tiny withdrawals, and the errors stack up, letting the attacker drain value by manipulating the pool's state.
Early analyses on X (like this one and another) blamed Bunni's unique rebalancing features, but the team clarified that wasn't the case—no rebalancing happened during the exploit.
Impact and Response
The hack drained about $8.4 million, but Bunni acted fast. They paused most operations except withdrawals, allowing LPs to pull out their funds safely. The team worked with auditors like Cyfrin (check their detailed gist) and others to analyze and fix the issue.
For users, it was a wake-up call: Always check protocol audits and understand the risks of providing liquidity, especially in newer setups like Uniswap v4 hooks.
Lessons Learned for DeFi and Meme Tokens
This exploit isn't just a Bunni story—it's a cautionary tale for the entire blockchain space, including meme token creators who rely on DEXes for liquidity. Meme tokens often launch on platforms like Uniswap, where similar vulnerabilities could wipe out communities overnight.
Key takeaways:
Rounding Matters: Always consider how rounding behaves in multi-step attacks. Favor the user or protocol consistently, but test for cumulative effects.
Audits Aren't Foolproof: Bunni had audits, but edge cases like this slipped through. Combine multiple auditors and use formal verification tools like those from Certora.
Flashloan Risks: These tools enable innovation but also attacks. Protocols should design with atomic operations in mind.
Community Transparency: Bunni's quick post-mortem and unpausing withdrawals built trust. Meme token projects should follow suit—honesty keeps the community strong.
In the meme token world, where hype can drive massive liquidity pools, understanding these technical pitfalls is crucial. It helps developers build safer launches and traders spot red flags.
Bunni vows to keep building, and with lessons like this, DeFi will get stronger. If you're tinkering with smart contracts for your next meme coin, remember @0xngmi's words: It's brutal out there. Stay vigilant, test rigorously, and maybe round in a way that doesn't bite back.