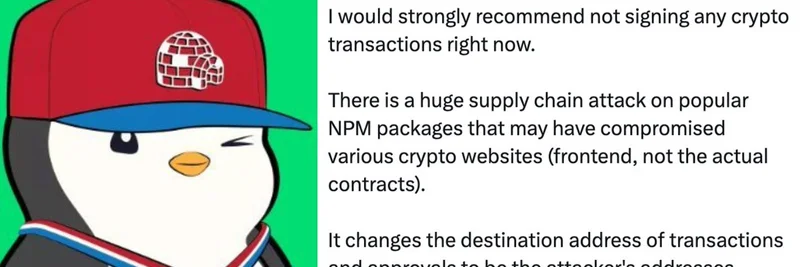
In the fast-paced world of crypto, where meme tokens can moon or rug in a heartbeat, staying safe is just as important as spotting the next big pump. Recently, a stark warning from developer @0xCygaar, shared by @DegenerateNews, has sent ripples through the community: hold off on signing any crypto transactions right now. This comes amid a huge supply chain attack on popular NPM packages that could have snuck malicious code into various crypto websites.
What Exactly Is Happening?
For those not deep in the dev side, NPM (Node Package Manager) is like a massive library where developers grab pre-built code snippets to speed up building apps. Packages like chalk, debug, and color—used in billions of downloads—are super common in web frontends, including those for crypto dApps and meme token launchpads.
According to reports from security firms like Semgrep and Socket, the attack started when a prolific maintainer known as Qix got phished. Hackers then pushed out tainted versions of these packages. The sneaky part? This malware doesn't mess with the smart contracts themselves but tweaks the frontend—the user-facing part of websites. When you go to approve a transaction or swap tokens, it swaps out the destination address for the attacker's wallet. Boom, your funds vanish without you realizing.
Even Ledger's CTO chimed in on CoinDesk, noting the scale: over a billion downloads potentially affected. Other analyses from ReversingLabs and CSO Online highlight how attackers are using Ethereum smart contracts to hide and deliver secondary malware, making it extra tricky to detect.
Why This Matters for Meme Token Enthusiasts
Meme tokens thrive on hype, quick launches, and community-driven trades—often on platforms built with these very NPM tools. Think about it: you're eyeing a new Solana meme coin, head to its website to mint or stake, and unknowingly approve a drain to a hacker's address. In the meme space, where rugs and scams are already rampant, this attack amps up the risk. Projects like those on Pump.fun or smaller DEXes might be vulnerable if their frontends pulled in compromised code.
Replies to the original post capture the vibe: one user joked about being "forced to $HODL now," while others shared tips like revoking approvals via tools such as Revoke.cash. It's a reminder that even in the degenerate world of memes, security can't be an afterthought.
How to Protect Yourself
While the dust settles, here's some straightforward advice:
- Pause All Activity: No signing, no approving, no minting. If it can wait, let it.
- Revoke Permissions: Head to a trusted site like Revoke.cash (double-check the URL!) and clean up any unnecessary approvals on your wallet.
- Use Hardware Wallets: If you must interact, stick to hardware like Ledger or Trezor, and always verify addresses manually.
- Update and Scan: Once patched versions roll out, update your dev environments carefully. For non-devs, clear browser caches and avoid suspicious sites.
- Stay Informed: Follow reliable sources like Aikido Security for updates on affected packages.
This isn't the first supply chain rodeo—remember the SolarWinds hack or past npm incidents? But in crypto, where money moves at light speed, the stakes are sky-high. As meme token traders, we're used to volatility, but let's not add unnecessary hacks to the mix. Keep an eye on official announcements, and remember: in blockchain, trust but verify—especially right now.
If you're building or trading meme tokens, bookmark resources like SC Media for deeper dives into these threats. Stay safe out there, degens!