Hey there, fellow blockchain enthusiasts! If you're diving into the world of smart contract development, especially on EVM-compatible chains, you've got to stay vigilant about security threats. Recently, there's been a buzz about proxy initialization poisoning attacks making a comeback, even on chains without traditional MEV like Base. Let's break this down step by step, drawing from a detailed thread by Mikko Ohtamaa (@moo9000), co-founder of Trading Protocol, to help you understand the risks and how to mitigate them.
First off, what's all this fuss about? A few weeks back, security researchers from teams like VennBuild, Dedaub, and others uncovered a massive campaign where hackers were sneaking backdoors into thousands of smart contracts, putting over $10 million at risk. These pros managed to rescue most of the funds before the bad guys struck, but it's a wake-up call for everyone in the space.
The attack revolves around proxy contracts, a clever workaround for upgrading smart contracts on EVM chains. You see, Ethereum Virtual Machine (EVM) tech from 2014 doesn't support native code upgrades—unlike newer chains like NEAR Protocol. So, developers use proxies: you deploy a proxy contract that points to an implementation contract holding the actual logic. Users interact with the proxy, which routes calls to the implementation. The owner can later "upgrade" by pointing the proxy to a new implementation.
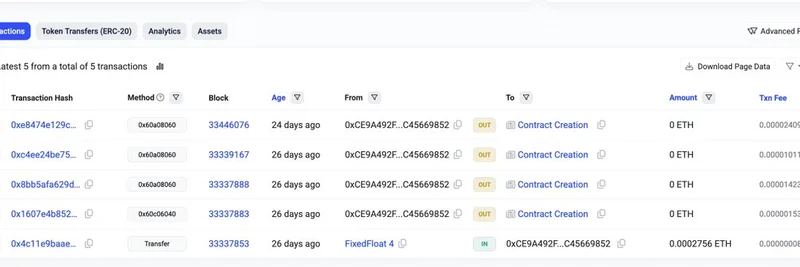
Here's where it gets tricky. The process typically involves two steps: deploying the proxy and then initializing it by setting the implementation address. Hackers exploit the gap between these steps. They monitor the chain for proxy deployments and front-run the initialization, setting their own malicious implementation. Boom—the proxy now points to code that lets them drain funds or wreak havoc.
In the past, attackers used Miner Extractable Value (MEV) to front-run transactions. MEV is basically when block producers reorder transactions for profit, often maliciously. Solutions like Shutter Network exist, but they're not widespread yet. What's new and alarming is that this is happening on Base, a layer-2 chain by Coinbase with a centralized sequencer. No MEV here since Coinbase controls transaction ordering. So, how are hackers pulling it off? Likely by running bots that watch for deployments or exploiting leaks in JSON-RPC providers—something that's happened before.
Even block explorers like Etherscan got fooled. Attackers set two different proxy slots in one front-running transaction: an old OpenZeppelin slot with a benign address (which Etherscan checks first) and the standard EIP-1967 slot with the malicious one. Sneaky, right?
The attacker on Base was funded via FixedFloat, a bridge popular among hackers, linking it to earlier campaigns. One victim, using Gnosis Safe for deployment, lost control just two blocks after deploying on Base.
So, how do you protect yourself? The key is to deploy and initialize in a single transaction. Tools like Foundry scripts can help, or check out this approach for inspiration. For multi-chain consistency, try the Deterministic Proxy Factory by emo.eth—it ensures the same addresses across chains.
On layer-2s like Base, always broadcast directly to the sequencer to avoid mempool leaks. Libraries like web3-ethereum-defi can handle this for you. For more details, dive into this Ethereum Stack Exchange discussion.
The full story, including block numbers, shows how close these calls can be. If you're a developer, join the Ethereum Security Researchers Telegram group for ongoing discussions and tips.
In the meme token world, where quick deployments are common, these vulnerabilities can spell disaster for your project. Stay safe, audit your processes, and remember: in blockchain, speed and security go hand in hand. Got questions? Drop them in the comments or hit up the experts!