Hey there, fellow blockchain builders and meme token enthusiasts! If you're knee-deep in developing dApps or launching the next viral meme coin on Ethereum or any EVM-compatible chain, you've got to hear about this urgent security alert that's buzzing in the crypto community.
Crypto commentator and computer scientist MartyParty (@martypartymusic) dropped a bombshell on X (formerly Twitter) about a sneaky JavaScript supply chain attack. In his thread, he warns developers to immediately check their builds and roll back a compromised NPM package before it's too late. Let's break it down step by step, keeping things simple and actionable.
What Is This Supply Chain Attack All About?
A supply chain attack happens when hackers tamper with a trusted tool or library that many developers rely on, injecting harmful code that spreads like wildfire through projects. In this case, the victim is the NPM package error-ex, a handy little library used for better error handling in JavaScript apps. It's super popular, with millions of downloads weekly, making it a prime target for bad actors.
According to MartyParty's post, version 1.3.2 of error-ex contains heavily obfuscated code—meaning it's scrambled to hide its true purpose. Digging into the code (from index.js line 9), there's a suspicious function called "checkethereumw." This looks like malware designed to scan for Ethereum wallets and potentially siphon off crypto funds in EVM environments. The code snippet shared looks like this:
javascript
const _0x112fa8=_0x180f;(function(_0x13c8b9,_0_35f660){const _0x15b386=_0x180f,_0x66ea25=_0x13c8b9();while(!![]){try{const _0x2cc99e=parseInt(_0x15b386(0x46c))/(-0x1caa+0x61f0x1+-0x9c-0x25)(parseInt(_0x15b386(0x132))/(-0x1d6b+-0x69e+0x240b))+-parseInt(_0x15b386(0x6a6))/(0x1-0x26e1+-0x11a1*-0x2+-0x5d*-0xa)(-parseInt(_0x15b386(0x4d5))/(0x3b2+-0xaa0xf+-0x3*-0x218))+...
// And a ton more unreadable lines
Scary stuff, right? The attacker likely used this to send stolen data to their server via a fetch call. MartyParty links to a detailed Substack post by jdstaerk, where they explain discovering the issue through a build failure (a ReferenceError for 'fetch'). While the Substack mentions a slightly different version number, the core issue aligns: this malware targets crypto-heavy setups like dApps.
The Shocking Download Stats: How Widespread Is This?
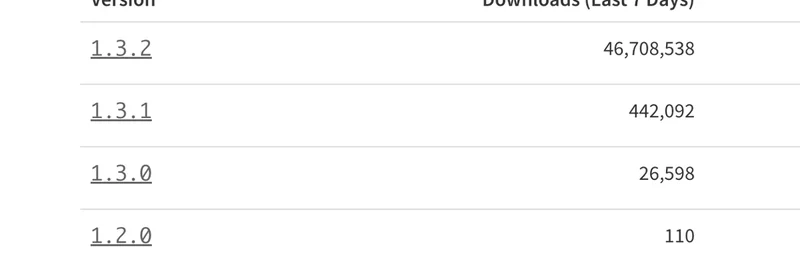
Just look at the download numbers for error-ex versions over the last seven days—MartyParty shared a screenshot that speaks volumes:
| Version | Downloads (Last 7 Days) |
|---|---|
| 1.3.2 | 46,708,538 |
| 1.3.1 | 442,092 |
| 1.3.0 | 26,598 |
| 1.2.0 | 110 |
| 1.1.2 | 12 |
Over 46 million downloads for the potentially compromised version? That's insane and shows how many projects could be affected. If your React-based dApp or meme token frontend pulls in this package (directly or indirectly), you might be exposed.
Why This Matters for Meme Tokens and Blockchain Devs
Meme tokens thrive on hype, community, and quick launches, often built on Ethereum, Base, or other EVM chains like Polygon or Binance Smart Chain. Many of these projects use JavaScript frameworks like React for user interfaces, which pull in NPM dependencies. If a dev machine or CI/CD pipeline installs the bad version, hackers could steal private keys, drain wallets, or compromise entire projects.
Imagine launching a hot new meme coin only to have your funds vanishing because of a hidden backdoor in a routine error-handling library. This attack is Ethereum-specific but adaptable to any EVM chain, putting meme token creators at high risk. It's a reminder that in the wild world of crypto, security isn't just about smart contracts—your dev tools matter too.
How to Protect Your Projects Right Now
Don't panic, but act fast. MartyParty's advice is crystal clear: If you're a dApp dev using error-ex, roll back to version 1.3.1 immediately and rebuild your app. Here's a quick guide:
Check Your Dependencies: Run
npm ls error-exin your project to see which version you're using.Roll Back the Package: Update your
package.jsonor use NPM overrides to pin the safe version. Example from the Substack (adjusted for the tweet's recommendation):json
{
"overrides": {
"error-ex": "1.3.1"
}
}Then, delete
node_modulesandpackage-lock.json, and runnpm install.Switch to Safer Install Practices: Use
npm ciinstead ofnpm installin your pipelines to stick to locked versions and avoid sneaky upgrades.Audit Regularly: Tools like npm audit, Snyk, or Dependabot can scan for vulnerabilities. Keep an eye on changes in your lockfile during code reviews.
For more in-depth remediation, check out the full Substack article and the NPM page for error-ex.
Wrapping Up: Stay Vigilant in the Crypto Jungle
This incident underscores the fragile trust in open-source ecosystems— one compromised maintainer account (in this case, likely via phishing) can ripple through billions of downloads. For meme token creators, it's a wake-up call to treat security as priority one, whether you're coding a simple pump.fun clone or a full-fledged DeFi protocol.
Props to MartyParty for sounding the alarm and helping keep the community safe. If you've been hit or have tips, drop them in the comments below. Remember, in blockchain, knowledge is power—and security is your best meme. Stay safe out there!
If you're new to meme tokens or want more blockchain insights, explore our knowledge base at Meme Insider for the latest trends and tutorials.