A huge security scare just rocked the JavaScript world, and it's got big implications for everyone in crypto, especially if you're trading meme tokens. If you've ever used a decentralized exchange (DEX) or connected your wallet to a web app, this could affect you. Let's break it down simply and see why one expert is calling for a shift to on-chain solutions.
The drama started on September 8, 2025, when a developer known as Qix- fell victim to a phishing email from a fake support address: support@npmjshelp. Hackers got hold of his NPM (that's Node Package Manager, the go-to spot for JavaScript libraries) credentials and pushed malicious updates to 18 popular packages. We're talking heavy hitters like chalk (for colorful console output), strip-ansi (removes ANSI codes from strings), color-convert, debug, error-ex, and ansi-styles. These libraries rack up over 2 billion downloads weekly, so the reach is massive.
What makes this scary for crypto folks? The malware injected is a "crypto clipper." It sneaks in and swaps wallet addresses in your apps. There are two main tricks: passively replacing addresses in dApps (decentralized applications) or actively hijacking transactions right before you sign them. It even uses something called the Levenshtein algorithm to make the fake addresses look super similar to yours—think one tiny character change that you might miss.
For meme token traders, this is a nightmare. Meme coins thrive on fast trades via platforms like Uniswap or Raydium, which often rely on JavaScript frontends. If your app pulls in one of these tainted libraries, boom—your SOL or ETH could end up in the hacker's pocket instead of that moonshot token. No funds have moved yet to the attacker's known wallets (like 0xFc4a4858bafef54D1b1d7697bfb5c52F4c166976 on Ethereum), but the potential for drains is real.
Developers spotted the issue when builds threw weird errors, like "fetch is not defined." Digging deeper revealed obfuscated code hiding crypto-targeted functions. The phishing domain was fresh, registered just days before, showing how quick these attacks can be.
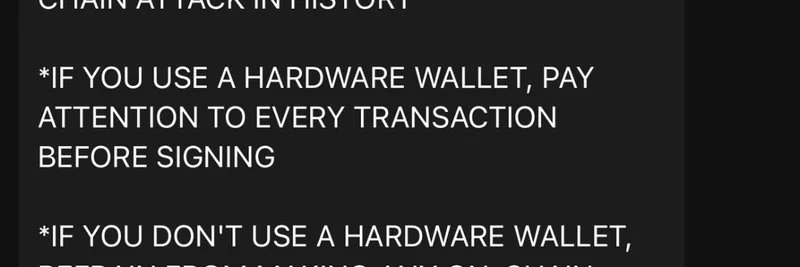
Ledger's CTO, Charles Guillemet, sounded the alarm early, warning about the supply chain attack and advising users to pause on-chain transactions unless using a hardware wallet. Hardware wallets add that extra layer where you manually verify transactions on the device, dodging the software tricks.
In response to this mess, crypto commentator MartyParty highlighted a key update: the hack actually stemmed from stolen GitHub credentials, not just NPM. He tweeted, urging blockchain projects to move Web2 code (traditional web stuff) onto the chain. "Github is a risk at this point from dev credential hacks," he said. His big idea? Require multisig Web3 signing for commits on any Web2 package that touches Web3. Multisig means multiple signatures needed for actions, like a group vote for code changes, adding security.
This aligns perfectly with meme token ecosystems, where community-driven projects often use open-source tools. Shifting to on-chain code could mean storing and verifying libraries directly on blockchains like Solana or Ethereum, reducing reliance on centralized platforms like GitHub.
To stay safe right now, especially if you're hunting the next big meme coin:
- Stick to hardware wallets and double-check every address before signing.
- In your projects, pin exact package versions in your package.json file to avoid auto-updating to bad ones.
- Use "npm ci" instead of "npm install" for cleaner, reproducible builds.
- Rotate your GitHub and NPM keys immediately if you're a dev.
The community caught this one fast, but it exposes how fragile our hybrid Web2-Web3 setup is. As meme tokens continue to explode in popularity, beefing up security isn't just smart—it's essential. Keep an eye on updates from sources like Ledger's blog or NPM's security alerts to stay ahead.