Hey folks, if you're deep into the world of meme tokens and blockchain, you've probably heard the buzz about a massive security breach shaking up the JavaScript scene. A thread from @StarPlatinumSOL on X breaks it down, and it's got serious implications for anyone trading or holding crypto, especially those fun, volatile meme coins. Let's dive into what happened, why it matters for the meme community, and how to protect yourself.
The Attack Unpacked
It all started on September 8, 2025, when hackers phished their way into the NPM account of a developer named Qix-. NPM, short for Node Package Manager, is basically the go-to repository for JavaScript libraries—think of it as a massive toolbox that developers pull from to build apps, including those decentralized apps (dApps) we use for swapping meme tokens on chains like Solana or Ethereum.
The attackers compromised 18 core packages, stuff like 'chalk' for colorful console outputs, 'strip-ansi' for cleaning text, and 'debug' for troubleshooting code. These aren't niche tools; they rack up over 2 billion weekly downloads. That's billions with a 'b'—meaning this hack could ripple through countless web and blockchain apps.
The phishing email came from a fake domain, support@npmjshelp, registered just days before. Once in, the hackers pushed malicious updates lightning-fast. The malware? A sneaky crypto clipper designed to steal your funds without you noticing.
How the Malware Works and Why It's a Nightmare for Crypto
This isn't your average virus. The payload has two main tricks:
Passive Address Swapping: It quietly replaces wallet addresses in dApps. You're copying what looks like your address, but it's been swapped with the hacker's.
Active Hijacking: During transactions, it intercepts and alters the destination address right before you sign off.
It even uses the Levenshtein algorithm—fancy math for measuring how similar two strings are—to swap your address with one that looks almost identical. One wrong character, and poof, your meme token gains go to the bad guys.
For meme token traders, this is especially risky. Meme coins often involve quick trades on platforms like DEXs (decentralized exchanges), where you're constantly connecting wallets and approving transactions. If your dev environment or app is tainted by these packages, you could lose everything in a blink.
The attacker's main Ethereum wallet is 0xFc4a4858bafef54D1b1d7697bfb5c52F4c166976, with backups like 0xa29eEfB3f21Dc8FA8bce065Db4f4354AA683c024. No funds moved yet, but that's cold comfort.
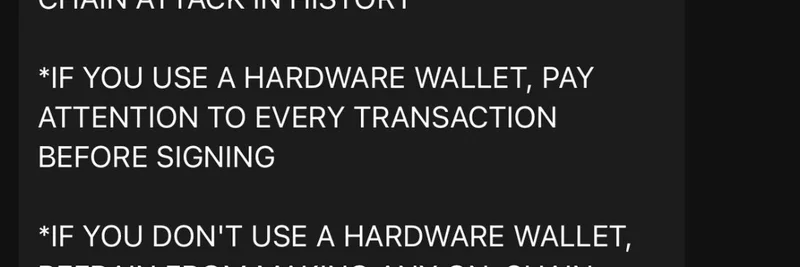
Ledger CTO's Urgent Warning
Charles Guillemet, CTO at Ledger, sounded the alarm in a quoted post: If you've got a hardware wallet (like a Ledger device), double-check every transaction before signing—you're mostly safe because the hardware verifies details offline. But if you're using software wallets? Hold off on any on-chain moves until this blows over. The malware might even snag your seed phrases directly.
This echoes broader crypto security chats, reminding us that even meme token fun comes with real risks. Remember the Ronin Network hack or those Solana wallet drains? Supply chain attacks like this could hit dApp frontends hard, where many meme launches happen.
Staying Safe in the Meme Token Wild West
The community spotted this quick—developers flagged weird errors like 'fetch is not defined' and dug into the obfuscated code revealing crypto-targeted functions. But it highlights how fragile our blockchain tools are.
Here's how to armor up, especially if you're building or trading meme tokens:
Hardware Wallets Are King: Use one for all transactions. It adds a physical layer of security that software can't match.
Pin Your Dependencies: In your package.json, lock in exact versions of libraries to avoid auto-updating to malicious ones.
Switch to 'npm ci': This command installs packages exactly as specified, ignoring local changes—safer than plain 'npm install'.
Rotate Keys Now: Change your GitHub and NPM credentials ASAP if you're a dev.
Verify Addresses Manually: Always paste and check wallet addresses character by character, especially for meme token airdrops or trades.
For more deets, check out the full thread on X or reports from security firms like Snyk.
This attack is a wake-up call for the blockchain space. Meme tokens thrive on hype and community, but security lapses can turn that into chaos. Stay vigilant, and let's keep building a safer crypto ecosystem together. If you've got tips or stories from this, drop them in the comments!