Unpacking the Morpho Labs Security Scare: What Happened?
On April 11, 2025, the DeFi community was rattled by a security issue involving Morpho Labs, a project known for its high-quality code and rigorous security practices, including 34 publicly listed audits (Morpho Docs). A user named Greysign (@greysign1) took to X to share a detailed investigation into the incident, revealing a critical vulnerability that contradicted Morpho’s initial claims. Let’s break down what happened, why it matters, and how you can protect yourself.
Morpho Labs, a decentralized finance protocol, rolled out a frontend update on April 10, 2025, aimed at improving transaction flows in their Morpho App. However, by 3:54 AM CET on April 11, a report flagged that some transactions were being incorrectly crafted, leading to a swift response from the Morpho team. They fixed the issue by 4:44 AM CET and communicated the update on X by 5:23 AM CET (Morpho Labs Update). Initially, Morpho claimed the problem was limited to the frontend, assuring users that funds in the Morpho Protocol were safe. But Greysign’s investigation revealed a deeper issue: the problem wasn’t just in the frontend—it was a contract-level vulnerability in Bundler3.
The Real Culprit: A Bundler3 Contract Vulnerability
Greysign initially suspected a frontend exploit, thinking hackers might have injected malicious code into the Morpho App to steal Permit2 signatures before transactions were submitted to the blockchain. Permit2 is a standard that allows users to approve token transfers securely, often used in DeFi to streamline interactions. However, after analyzing the attack transactions, Greysign concluded the issue was in the Bundler3 contract itself, not the frontend.
Bundler3, as explained in Morpho’s documentation (Introducing Bundler3), is an immutable, open-source contract designed to handle multiple contract calls in a single transaction—a feature called multicall. This is useful in DeFi because externally owned accounts (EOAs), like your typical Ethereum wallet, can’t execute multiple actions simultaneously. Bundler3 was meant to solve this by batching calls, such as approving a token transfer and executing a trade in one go. It was audited by Spearbit and OpenZeppelin and even formally verified by Certora, with a $1.5M bug bounty program on Immunefi and Cantina. So, what went wrong?
The vulnerability lies in how Bundler3’s multicall function was implemented. Unlike a basic multicall, which simply batches calls, Bundler3 allowed users to pass arbitrary calls to be executed on its behalf. However, it lacked proper restrictions, meaning attackers could manipulate the calls. Here’s how the exploit worked:
- A user would interact with Bundler3, approving it to manage their tokens via a Permit2 signature.
- The user’s transaction, including the Permit2 signature, would enter the mempool—the waiting area for Ethereum transactions.
- An MEV (Maximum Extractable Value) bot, which scans the mempool for profitable opportunities, would spot the transaction. MEV bots are automated systems that exploit transaction ordering for profit, often through tactics like frontrunning or sandwiching (Blocknative on MEV).
- The bot would frontrun the user’s transaction by submitting its own transaction with a higher gas fee, using the same Permit2 signature to execute a
TransferFromcall via Bundler3’s multicall. This redirected the user’s tokens to the attacker’s address.
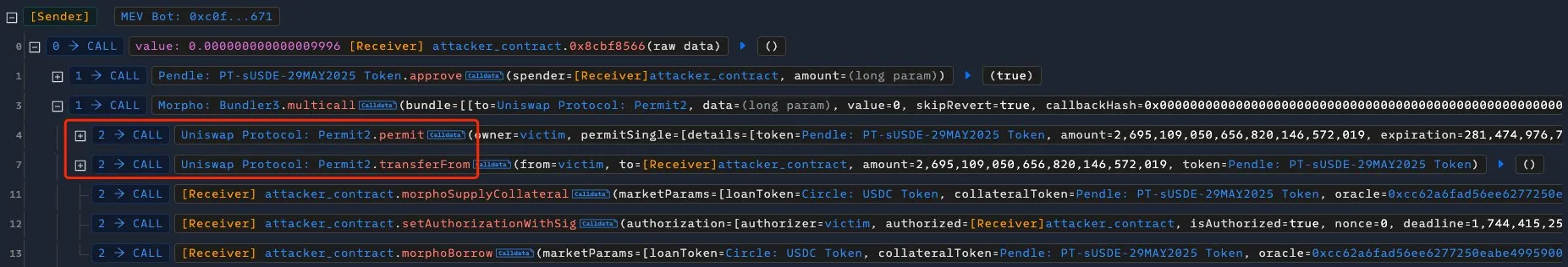
Greysign shared a screenshot of an attack transaction, highlighting the malicious TransferFrom call in red:
The core issue? Bundler3’s multicall didn’t ensure atomic execution—meaning the batched calls weren’t guaranteed to execute as a single, uninterruptible unit. Attackers could tamper with the calls, exploiting the lack of restrictions to steal tokens.
Morpho’s Response and Fix: A Step Back to Bundler2
Morpho Labs quickly paused the Morpho App frontend after identifying the issue and later claimed the frontend was safe, with no further action needed from users. However, Greysign’s findings suggest Morpho downplayed the severity by framing it as a frontend problem. In reality, the fix involved abandoning Bundler3 entirely.
Greysign noted that Morpho reverted to using Bundler2, an older version of the contract (address: 0x4095f064b8d3c3548a3bebfd0bbfd04750e30077). Unlike Bundler3, Bundler2 has stricter controls, wrapping functions and limiting the types of calls that can be executed. This prevents attackers from passing arbitrary calls, effectively closing the vulnerability. Greysign confirmed this by testing the updated Morpho App, which now calls Bundler2:
Interestingly, Bundler3 was deployed 74 days prior but only became active for about 10 hours, with most transactions occurring 18 hours before the incident. Morpho’s decision to switch to Bundler3 in the first place remains unclear, especially since Greysign couldn’t find any audit reports specifically addressing Bundler3’s multicall implementation in Morpho’s 2024 reports.
Why This Matters: A Pattern Vulnerability in DeFi
This wasn’t a one-off bug tied to Morpho’s business logic—it’s a pattern vulnerability that could affect other DeFi protocols using similar multicall implementations. The lack of atomic execution in Bundler3’s multicall allowed attackers to exploit the mempool, a common attack vector in Ethereum’s transaction lifecycle. Greysign demonstrated that other transactions involving Bundler3 were also vulnerable, simulating attacks to confirm tokens could still be stolen:
This incident highlights the risks of token approvals in DeFi. When you approve a contract like Bundler3 to manage your tokens, that approval persists until revoked. If the contract has a vulnerability, attackers can exploit it to drain your funds, even long after your initial interaction (Dexola on Token Approvals).
How to Stay Safe: Revoke Approvals and Avoid Bundler3
Greysign’s final warning is critical: if you’ve interacted with Bundler3 (address: 0x6566194141eefa99Af43Bb5Aa71460Ca2Dc90245) and signed a Permit2 approval, your tokens are at risk. MEV bots can still frontrun your transactions in the mempool and steal your funds. Here’s what you should do:
- Revoke Token Approvals: Use a service like Revoke.cash to check and revoke any approvals you’ve given to Bundler3. This prevents attackers from using your existing approvals to steal tokens.
- Avoid Bundler3 Interactions: Do not interact with the Bundler3 contract until Morpho confirms a permanent fix or deprecates it entirely.
- Check Your Transaction History: Review your wallet’s transaction history for any interactions with Bundler3, especially if you used the Morpho App around April 10-11, 2025.
Fortunately, funds already deposited in the Morpho Protocol itself are safe, as the vulnerability only affects interactions with Bundler3, not the core protocol.
The Bigger Picture: Transparency and Trust in DeFi
Greysign expressed disappointment in Morpho Labs, a team they previously admired for their code quality and security focus. The lack of transparency—framing the issue as a frontend problem when it was a contract vulnerability—eroded trust. Morpho’s promise to release a detailed post the following week (Morpho Labs Update) was met with skepticism, with users like 0xSimon questioning the delay (0xSimon’s Reply).
This incident underscores the importance of transparency in DeFi. When security issues arise, clear and honest communication is crucial to maintaining user trust. It also highlights the need for rigorous testing of contract upgrades, especially when replacing a secure implementation (Bundler2) with a new one (Bundler3) that introduces unforeseen risks.
Final Thoughts
The Morpho Labs security incident of April 2025 is a stark reminder of the complexities and risks in DeFi. While Morpho acted quickly to mitigate the issue, the initial miscommunication and the nature of the vulnerability raise important questions about contract design and user safety. Thanks to Greysign’s thorough investigation, the community now has a clearer picture of what went wrong and how to protect themselves.
If you’re a Morpho user, take action now to revoke any Bundler3 approvals and stay cautious. For the broader DeFi space, this incident is a call to prioritize atomic execution in multicall implementations and to communicate transparently during crises. Stay safe, and always double-check the contracts you interact with!