If you're keeping tabs on the wild world of meme tokens and crypto projects, you've probably heard the buzz about the recent attack on the NGP token. Issued by the New Gold Protocol, this incident on the Binance Smart Chain (BSC) resulted in a whopping $2 million in losses. Thanks to insights from blockchain security firm BlockSec Phalcon, we have a clear picture of how it all went down. Let's break it apart step by step, explaining the tech in simple terms so even if you're new to this, it makes sense.
What Happened to NGP Token?
BlockSec Phalcon's monitoring system spotted the attack just hours ago on September 18, 2025. It was a classic price manipulation exploit, where the attacker twisted the token's own rules to their advantage. BSC, for those unfamiliar, is a blockchain platform similar to Ethereum but known for lower fees and faster transactions—perfect for DeFi and meme token trading, but also a hotspot for vulnerabilities.
The root cause? Two major design flaws in the NGP smart contract:
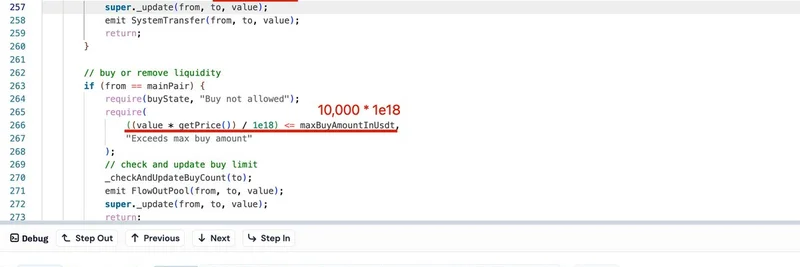
Bypassing Buy Limits: The token had restrictions on how much you could buy at once (maxBuyAmountInUsdt) and cooldown periods between purchases. But by setting the recipient address to a "dead" address (like 0x000...dEaD, a common burn address in crypto), the attacker sidestepped these entirely.
Fee Sync Abuse: When selling NGP, the contract updates (syncs) the liquidity pool to account for fees. This process was exploitable to artificially pump the token's price.
How the Attack Unfolded
The attacker played it smart, using multiple accounts to pull this off without raising immediate red flags. Here's the play-by-play:
Initial Purchases at Low Prices: They started by buying NGP tokens cheaply, spreading it across accounts to avoid detection.
Price Inflation via Swaps: Next, large swaps of BUSD (a stablecoin pegged to the US dollar) for NGP on the PancakePair liquidity pool. PancakeSwap is BSC's go-to decentralized exchange, similar to Uniswap on Ethereum. By routing transfers to the dead address, they ignored the buy limits and cooldowns, amassing a huge stack of NGP without restrictions.
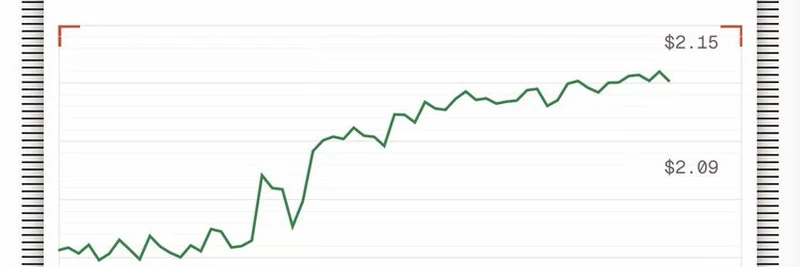
- Draining the Pool: With their NGP hoard, they sold back into the pool, draining BUSD. Fees were deducted for things like treasury and rewards, but this left the pool with barely any NGP reserves. The result? A massive price spike due to scarcity, allowing the attacker to profit big from the manipulation.
From reports, the attacker funneled the stolen funds—around 443.8 ETH—into Tornado Cash, a privacy mixer that makes tracking harder. The NGP price plummeted 88% in just an hour, wiping out value for holders.
Lessons for Meme Token Enthusiasts
This NGP exploit highlights why auditing smart contracts is crucial, especially for meme tokens that often launch quickly to ride hype waves. Flaws like unchecked address inputs or sync mechanisms can turn a project into a hacker's playground. If you're trading or holding tokens on BSC, always check for audits from reputable firms like BlockSec or PeckShield.
For more details, check out the original alert from Phalcon on X. Stay safe out there in the crypto jungle—knowledge is your best defense against these kinds of attacks. If you've got thoughts on this or similar exploits, drop them in the comments!