In the fast-paced world of blockchain and crypto, staying secure is paramount, especially for meme token enthusiasts who often tinker with code and dApps. Recently, a supply chain attack hit the NPM registry, compromising popular JavaScript packages like chalk and debug.[0] These libraries, boasting over a billion downloads, were rigged with malware designed to hijack crypto wallets by swapping out wallet addresses during transactions.[1]
Crypto commentator and computer scientist MartyParty shared a detailed look at the exact malware code on X, highlighting how attackers masked their wallet addresses across various blockchain networks.[0] According to his post, only about $158 has been stolen so far, a surprisingly low amount given the potential reach. Most affected projects have already updated their status, confirming they're unaffected or have rebuilt their systems.
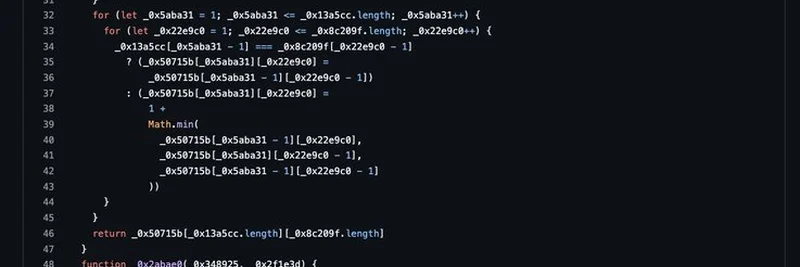
Here's a glimpse into the malicious code shared in the thread:
The code essentially overrides Ethereum's request methods to redirect funds to the hackers' addresses on chains like Ethereum, Binance Smart Chain, and others. It's a clever but dangerous trick that underscores the risks in open-source dependencies.
Community Response and Lessons for Meme Tokens
The crypto community responded swiftly, with Ledger's CTO warning about the attack's scale.[5] In MartyParty's thread, replies poured in praising the quick detection—some even joked that the hacker provided free QA testing for NPM packages.
For meme token creators and users, this incident is a wake-up call. Many meme projects rely on JavaScript for front-end interfaces connecting to wallets via libraries like Web3.js. A compromised dependency could spell disaster, draining funds from unsuspecting degens. To stay safe:
- Always verify package versions and use tools like npm audit.
- Consider using hardware wallets like Ledger for added security.
- Keep an eye on updates from trusted sources and rebuild projects if needed.
As MartyParty emphasized, "Open Source community. Stay vigilant. Prevent this happening again." In the meme token space, where hype moves fast, security should always come first.
Check out the original thread on X for more details and join the discussion.