In the fast-paced world of blockchain development, especially for those launching meme tokens, using upgradeable contracts via proxies is a popular way to keep things flexible. But as highlighted in a recent breakdown by Nethermind Security, even established libraries like OpenZeppelin can lead to pitfalls if not handled carefully. Let's dive into this vulnerability example and unpack what went wrong—and how to fix it.
Understanding Proxy Contracts and UUPS
First off, a quick primer for newcomers: Proxy contracts in Solidity act like middlemen. They hold the storage and user-facing address, while delegating logic to an implementation contract. This setup allows upgrades without changing the contract address, which is handy for fixing bugs or adding features in meme token projects where community feedback might demand quick changes.
OpenZeppelin's UUPS (Universal Upgradeable Proxy Standard) is a flavor of this pattern. It builds on ERC-1967 proxies but puts the upgrade logic in the implementation itself, making it more gas-efficient. Key players here include contracts like OwnableUpgradeable, PausableUpgradeable, and UUPSUpgradeable.
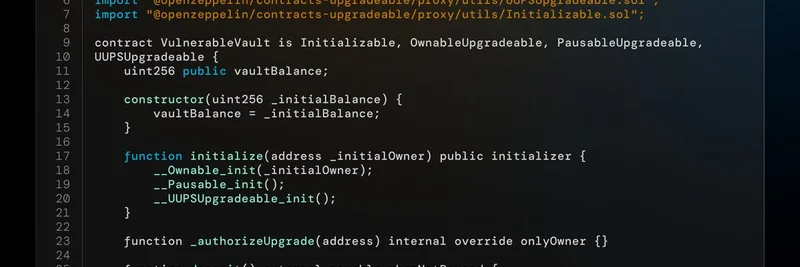
In the example shared by Nethermind Security on X, we see a VulnerableVault contract that inherits these traits. It seems straightforward, but there are hidden dangers.
Spotting the Issues in Deployment and Initialization
The code poses a challenge: Can you spot what's off? The contract has a constructor that sets an initial vaultBalance, and an initialize function that handles ownership, pausability, and UUPS setup.
Here's the breakdown:
Missing Initializer Lock in Constructor: In upgradeable contracts, the implementation (logic) contract should never be usable on its own—it's meant to be called via the proxy. To prevent this, OpenZeppelin recommends calling
_disableInitializers()in the constructor. Without it, an attacker could initialize the implementation directly, taking ownership and potentially wreaking havoc. For meme token devs, this could mean losing control of your token's treasury or upgrade rights.Storage Initialization in Constructor: The constructor sets
vaultBalance = _initialBalance. But remember, when deployed behind a proxy, the constructor runs on the implementation contract, not the proxy. So, this balance ends up in the implementation's storage, not the proxy's where it belongs. Transactions through the proxy won't see this value, leading to incorrect behavior—like a vault that appears empty when it shouldn't.
The fix? Move that balance setup to the initialize function, which executes in the proxy's context via delegatecall. This ensures storage changes happen where they matter.
Why This Matters for Meme Token Creators
Meme tokens often launch quickly, sometimes using templates or libraries without deep audits. Upgradeability sounds great for evolving your project based on viral trends, but skimping on these details can lead to exploits. We've seen similar issues in DeFi protocols, and meme ecosystems aren't immune—attackers love low-hanging fruit.
Nethermind's insight reminds us: Always secure your implementations. Call _disableInitializers() in constructors, and keep state initialization in upgrade-safe functions.
Best Practices to Secure Your Proxies
To avoid these traps:
Audit Your Inheritance: When mixing traits like
Initializable,OwnableUpgradeable, etc., ensure initialization order is correct to prevent re-initialization attacks.Test in Proxy Context: Use tools like Hardhat or Foundry to simulate proxy deployments. Verify storage slots align and initializers work as expected.
Follow OpenZeppelin Guidelines: Check their upgradeable contracts docs for the latest patterns.
By staying vigilant, you can build more robust meme tokens that stand the test of time—and hacks. If you're diving into Solidity for your next project, lessons like this are gold. What other proxy gotchas have you encountered? Share in the comments!