Hey folks, if you're deep into the world of blockchain and meme tokens, you've probably heard the buzz about the recent hack hitting Seedify Fund. For those not in the know, Seedify is a popular launchpad for gaming and metaverse projects, with their native token SFUND powering the ecosystem. But on September 23, 2025, things took a nasty turn when their bridge contracts got compromised. Let's break it down step by step, keeping it simple and straightforward.
It all started with an announcement from Meta Alchemist, the founder of Seedify Fund. In a post on X, they revealed that one of their SFUND bridges had been drained in a hack. They emphasized that the contracts had been audited and running smoothly for over three years, and they were already reaching out to LayerZero—the tech behind their cross-chain setup—for help. The team promised to work with authorities and cybersecurity experts to track down the culprits. You can check out the original announcement here.
Shortly after, blockchain security firm BlockSec's Phalcon team jumped in with a detailed analysis on X. According to their thread, the attack spanned multiple chains and stemmed from what looks like a private key compromise. Private keys are essentially the secret codes that control access to crypto wallets and smart contracts—if someone steals yours, they can wreak havoc.
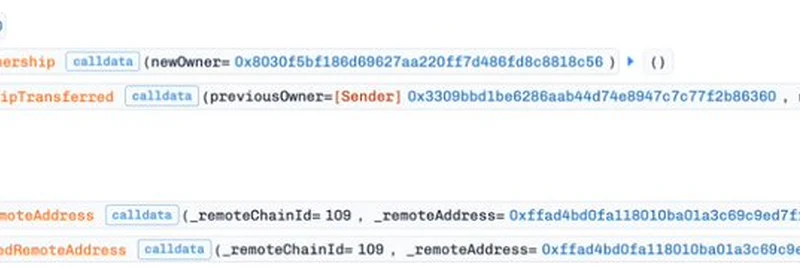
Here's how it went down: The attacker, operating from address 0x8030f5bF186d69627aA220FF7d486fd8c8818c56, first seized ownership of the SFUND_OFTv1 contracts on destination chains like Base. OFTv1 stands for Omnichain Fungible Token version 1, a standard from LayerZero that lets tokens move seamlessly across different blockchains.
Once in control, the hacker used the setTrustedRemoteAddress function to designate a malicious contract (0xffad4bD0fA118010bA01a3C69C9Ed7fF460E943e) as a trusted source. This sneaky move allowed fake cross-chain messages from a source chain, such as Polygon, to be validated and executed on the destination chain. The result? The attacker minted or transferred SFUND tokens illicitly and swapped them for other assets, pocketing the profits.
Phalcon outlined the key steps in their analysis:
Ownership takeover: The hacker transferred control of the contract to their address. See the transaction details on Base here.
Setting the malicious trusted remote: This updated the contract to trust the attacker's fake address for cross-chain comms. Check it out here.
Cross-chain request from Polygon: The fraudulent message was sent to trigger the exploit. View the transaction here.
Profits cashed in on Base: The attacker ended up with SFUND tokens, which they likely dumped for stablecoins or other cryptos.
To give you a visual, here's a screenshot from Phalcon's analysis showing the ownership transfer and trusted address setup in action:
This incident highlights the ongoing risks in cross-chain bridges, which are prime targets for hackers due to the massive value they handle. Even with audits, a single private key leak can undo years of security measures. For meme token projects, which often rely on similar bridging tech for liquidity across chains, this is a wake-up call. Always diversify your holdings, use hardware wallets for keys, and stay vigilant about project updates.
Seedify has committed to a full investigation, and we'll keep an eye on any recoveries or further details. In the volatile world of crypto, staying informed is your best defense. If you're building or investing in meme tokens, consider how these exploits could impact your favorites—knowledge is power!