In the fast-paced world of decentralized finance (DeFi), security remains a top concern, especially on chains like Arbitrum where protocols handle millions in user funds. Recently, Sharwa Finance, a platform allowing users to maximize exposure to ETH and WBTC through leveraged positions with built-in liquidation protection, fell victim to an exploit. The attack targeted its margin trading features, leading to losses in its USDC and WBTC liquidity pools. Let's break down what happened, how the attackers pulled it off, and what it means for the broader crypto ecosystem—including meme token enthusiasts who often dip into DeFi for amplified trades.
The Announcement and Initial Response
On October 20, 2025, Sharwa Finance took to X (formerly Twitter) to announce the breach: "@SharwaFinance has been exploited. The $USDC and $WBTC liquidity pools were affected. Trading is temporarily paused. All users who lost funds during the attack will be 100% refunded." This quick response aimed to reassure users, promising full refunds for those impacted.
However, security firm BlockSec's Phalcon team noted that additional suspicious transactions occurred hours after the pause, suggesting the same vulnerability was exploited multiple times. According to their analysis, two main attackers profited handsomely—around $61K and $85K respectively—through a combination of leveraged borrowing and sandwich attacks.
Understanding the Exploit: A Step-by-Step Breakdown
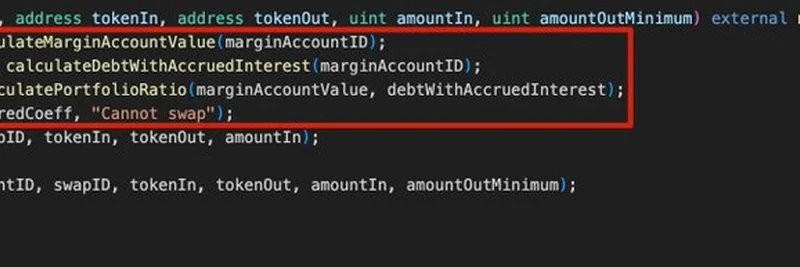
Sharwa Finance enables users to open long or short positions on assets like WBTC and ETH using the same asset as collateral, offering up to 10x leverage. The protocol integrates options for liquidation protection, but a critical flaw in its MarginTrading contract's swap() function opened the door for manipulation.
The root cause? An improper insolvency check. In simple terms, insolvency happens when a borrower's debt exceeds their collateral value, risking the protocol's solvency. The swap() function, which handles exchanging borrowed assets (e.g., from WBTC to USDC), only checked the account's solvency before executing the swap. This left a window for attackers to manipulate prices during the swap process without triggering the check afterward.
Here's how the attackers operated:
Create a Margin Account: The attacker deposits collateral (e.g., USDC) and borrows more assets via leverage to open a position, like going long on WBTC.
For example, in one transaction (view on Arbiscan), the attacker used a flash loan of 40 million USDC, deposited it, borrowed about 39.95 million USDC, swapped it for roughly 0.362 WBTC, and increased their long position.
Launch the Sandwich Attack: In a follow-up transaction, the attacker uses a flash loan to manipulate the market price on Uniswap V3 (which Sharwa trusted for quotes).
- First, swap a large amount of the asset (e.g., WBTC to USDC) to drive down the price.
- Then, close the leveraged position, selling at the artificially low price and leaving the protocol with bad debt.
- Finally, swap back (USDC to WBTC) at the depressed price to pocket the difference.
A key attack transaction (view on Arbiscan) shows this in action: A flash loan of 37 WBTC, large sell to drop the price, position closure selling 0.362 WBTC for about 2.075 million USDC (at a bad rate), repayment of only part of the debt, and buying back WBTC cheaply.
Another attacker followed a similar pattern, starting with margin account creation (view on Arbiscan).
Independent analyst Weilin Li echoed this, noting the protocol's blind trust in Uniswap V3 prices allowed atomic sandwich attacks, where the manipulation and exploit happen in one transaction.
The highlighted code shows the calculations and require statement happening before the actual swap, missing post-swap solvency verification.
Attacker Details and Profits
- Attacker 1 (0xd356c82e0c85e1568641d084dbdaf76b8df96c08): Executed multiple attacks, netting ~$61K.
- Attacker 2 (0xaa24987bab540617416b77c986f66ae009c55795): One attack, ~$85K profit.
These figures come from on-chain analysis by Phalcon, with the total drain around $146K. While not massive compared to some DeFi hacks, it underscores ongoing risks in leveraged protocols.
Lessons for DeFi and Meme Token Traders
Exploits like this aren't isolated to traditional assets like WBTC or ETH—they highlight vulnerabilities that could affect meme token ecosystems too. Many meme projects build on DeFi primitives for liquidity and trading, and similar flaws in borrowing or swapping could lead to flash loan attacks or price manipulations, eroding trust and value.
For blockchain practitioners, key takeaways include:
- Post-Action Checks: Always verify state after external calls, like swaps, to prevent manipulation.
- Oracle Diversity: Relying solely on one DEX like Uniswap V3 for prices invites sandwiches; integrate multiple oracles or TWAP (time-weighted average price) mechanisms.
- Audits and Pauses: Sharwa paused trading quickly, but additional attacks post-pause show the need for robust emergency responses.
As Meme Insider, we're keeping an eye on how such incidents influence meme token volatility and adoption. If you're trading leveraged positions on any chain, double-check protocol audits and consider diversification.
Stay vigilant in the crypto space—security is everyone's responsibility. For more on blockchain exploits and meme token insights, explore our knowledge base at meme-insider.com.