In the fast-paced world of Solana development, where high-speed transactions meet innovative DeFi tools, even a tiny oversight in code can open the door to major exploits. That's exactly what happened during an audit of MetaDAO's launchpad back in March—a subtle bug involving Program Derived Addresses (PDAs) that could let attackers siphon off freshly minted tokens. As part of the "Advent of Bugs" series from Solana security firm Accretion, this Day 1 revelation shines a light on PDA impersonation, a vulnerability that's a stark reminder for every blockchain builder to double-check their signer validations.
If you're knee-deep in Solana smart contracts or just dipping your toes into meme token launches on platforms like this, stick around. We'll break down what went wrong, walk through the attack step by step, and share the key lessons to keep your projects secure. No PhD required—just clear, straightforward insights to level up your defenses.
The Setup: A Launchpad's Trust in PDAs
MetaDAO's launchpad is designed to make token launches smooth and decentralized, much like the viral meme coin drops we're seeing explode across Solana. When initializing a new launch, the program creates a special account called the launch_signer. This isn't just any account—it's a PDA derived from the launch's key and a fixed seed ("launch_signer"). PDAs are Solana's way of creating "signer" accounts without private keys, using deterministic seeds to ensure they're controlled solely by the program logic.
The idea is simple: The launch_signer PDA acts as the mint authority for the new token. It signs off on minting initial tokens to a designated account, kickstarting the launch. To do this securely, the program uses Solana's invoke_signed function, which lets it "sign" on behalf of the PDA using the provided seeds.
But here's where things got slippery. The instruction didn't explicitly verify that the provided launch_signer account actually matched the expected PDA address. Instead, it trusted that passing the seeds into invoke_signed would handle everything. Spoiler: It didn't.
The Bug Exposed: Impersonating the Signer
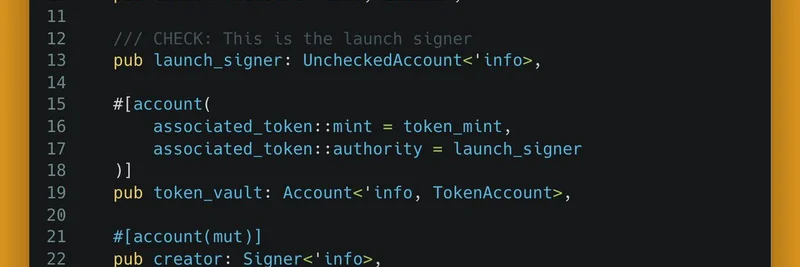
Accretion's auditors spotted the gap: The program marked the launch_signer as an unchecked account (UncheckedAccount), meaning no built-in validation on its address. This allowed any arbitrary Solana account to be passed in—as long as it was a top-level signer in the transaction and matched the mint's authority.
Why does this matter? In Solana, when you use invoke_signed with mismatched seeds, the function doesn't fail if the account is already signing the outer transaction. The seeds get ignored, and the real signature from the attacker's keypair takes over. Boom—impersonation achieved.
This isn't some edge-case theoretical risk. It's a backdoor straight to the token mint.
The Attack in Action: Stealing Tokens Before Launch
Imagine you're an attacker eyeing a hot new meme token launch. Here's how you'd exploit this, laid out in plain steps:
Prep Your Trap: Create a new mint account and set your own keypair (let's call it K) as the mint authority. Then, whip up a token account owned by K to receive the loot.
Trigger the Init: Call the
InitializeLaunchinstruction, passing K as thelaunch_signer. Make sure K signs the top-level transaction—easy since you control it.Mint the Backdoor Supply: The program happily mints tokens to your K-owned account, thinking it's signing via the PDA seeds. But nope—your keypair's signature does the heavy lifting, and the seeds are sidelined.
Cover Your Tracks: To avoid raising alarms, transfer most of the stolen tokens back, hand over the mint authority to the real PDA, and let the launch proceed as planned. You've got your illicit allocation, and the project thinks everything's fine.
In a meme token world where launches can pump millions in hours, this could mean snagging a whale-sized share before the community even notices. It's the kind of stealthy exploit that turns "to the moon" into "to the attacker’s wallet."
(For a visual dive into the code snippet highlighting the missing check, check out the annotated Rust code from the thread below.)
Why This Happens: A Quick Primer on Solana's Signing Quirks
If PDAs are new to you, think of them as program-controlled "ghost signers." They're derived from seeds (like ["launch_signer", launch.key()]) using find_program_address, ensuring only the program can "sign" for them via seeds in CPI (Cross-Program Invocations).
But Solana's flexibility cuts both ways. invoke_signed relies on the seeds to bump the PDA's address off the ed25519 curve, allowing programmatic signing. Without an explicit address check (e.g., require_keys_eq!(launch_signer.key(), expected_pda)), an attacker can swap in their own signer. The second image from the thread illustrates the full instruction flow, including the unchecked mint.
It's a classic case of "trust, but verify"—or in code terms, always verify.
Lessons for Solana Devs and Meme Token Builders
Accretion's fix? Simple: Add a check to ensure the passed launch_signer matches the derived PDA. No more impersonation parties.
Broader takeaways for anyone building on Solana—especially in the wild west of meme tokens and launchpads:
Always Validate PDAs: When using
invoke_signed, compute the expected PDA and assert it equals the provided account. It's cheap and bulletproof.Ditch Unchecked Accounts Where Possible:
UncheckedAccountis handy for flexibility, but pair it with explicit checks for signers.Audit Early, Audit Often: As the thread notes, this bug slipped through initial reviews. Firms like Accretion are spotting these gems—consider one before your next launch.
Test the Edges: Simulate attacks with tools like Solana's
solana-program-testto catch signer mismatches.
In the meme token ecosystem, where hype drives value faster than code reviews, these vulnerabilities can make or break a project. MetaDAO patched this post-audit, but stories like this keep the community sharp.
Wrapping Up: Security Accretes, Bugs Don't Have To
The "Advent of Bugs" series is off to a crackerjack start, reminding us that Solana's speed doesn't excuse sloppy security. Kudos to @r0bre and the Accretion team for sharing this—it's gold for devs chasing secure, scalable launches.
Got a Solana project brewing? Drop your thoughts in the comments: Ever hit a PDA snag? What's your go-to fix? And if you're auditing meme tokens at Meme Insider, hit us up for the latest on secure launches.
Stay vigilant out there—because in blockchain, one unchecked signer can launch a thousand exploits.