In the fast-paced world of blockchain, where a single miscalculation can lead to millions in losses, understanding complex bugs is crucial. Recently, Hari Krishnan, a key figure in the Solidity community and CEO at Spearbit, sparked a fascinating discussion on X with a simple question: "What's the most complex bug/exploit you've seen? I'm looking for particularly tricky bugs around math or rounding."
The responses poured in from security researchers and developers, highlighting some mind-bending exploits that revolve around mathematical intricacies and rounding errors. These stories aren't just thrilling—they offer valuable lessons for anyone building or investing in meme tokens, where smart contract security can make or break a project. Let's break down the highlights from the thread, explaining each in straightforward terms.
KyberSwap Elastic Exploit: Precision Gone Wrong
One standout mention came from zerosnacks.eth, pointing to the November 2023 KyberSwap Elastic hack that drained about $54.7 million. At its core, this exploit abused the platform's Concentrated Liquidity Market Maker (CLMM) and its Reinvestment Curve, which compounds fees for liquidity providers.
Here's how it unfolded: The attacker used flash loans to manipulate the pool's price (represented as sqrtP, the square root of the price scaled by 2^96). By adding and removing liquidity in precise amounts, they tricked the system into miscalculating token swaps across price boundaries (ticks). A bug in the calcReachAmount function overestimated tokens due to reinvestment liquidity inclusion, causing the protocol to skip updating liquidity when crossing ticks. This led to "duplicated" liquidity, letting the attacker swap back for massive profits.
The tricky part? It all hinged on precision issues and rounding in sqrtP calculations—tiny discrepancies that ballooned into huge gains. For meme token creators, this underscores the dangers in custom liquidity models. Always audit math-heavy functions! Check out the full deep dive here.
Bunni Hack: When Rounding Directions Betray You
Philogy chimed in with the recent Bunni hack, which siphoned $8.4 million just days ago. Bunni, a DeFi protocol on Ethereum and Unichain, fell victim to a rounding error in how it updates idle balances during withdrawals.
The attacker borrowed 3 million USDT via flash loan, skewed the USDC/USDT pool price to extremes, reducing USDC balance to a mere 28 wei. Then, through 44 tiny withdrawals, they exploited rounding that disproportionately slashed the liquidity estimate for USDC while keeping the USDT side intact. This created "ghost liquidity," allowing oversized swaps and profits.
The lesson? Rounding directions safe for single ops can chain into disasters. Bunni's post-mortem notes that isolated safe rounds became exploitable in sequence. Meme token projects using liquidity pools: Test multi-step scenarios rigorously. More details in Bunni's blog post.
Aztec Plonk Verifier '0 Bug': Zero-Knowledge Nightmares
Vishal Singh highlighted the Aztec Plonk verifier "0 bug," a vulnerability in Aztec's zero-knowledge proof system. Plonk is a zk-SNARK used for privacy-preserving transactions, but this bug allowed forging proofs by exploiting how zero is handled in elliptic curve math and Fiat-Shamir challenges.
Essentially, ambiguity in treating 0 as the point at infinity (or not) per the Plonk paper let attackers manipulate challenges and polynomials to pass invalid proofs. Public inputs weren't fully hashed, enabling adjustments for forged validity.
This one's ultra-tricky, involving advanced crypto math like bilinear pairings and polynomial commitments. For blockchain practitioners, especially in privacy-focused meme tokens, it highlights implementation pitfalls in ZK tech. The bug was patched, but see the exploit details for a deep read.
MIM_Spell Attack: Shares Manipulation Mastery
Misbahu referenced a detailed thread on the MIM_Spell (Abracadabra) attack from January 2024, where an attacker drained funds via borrow shares manipulation.
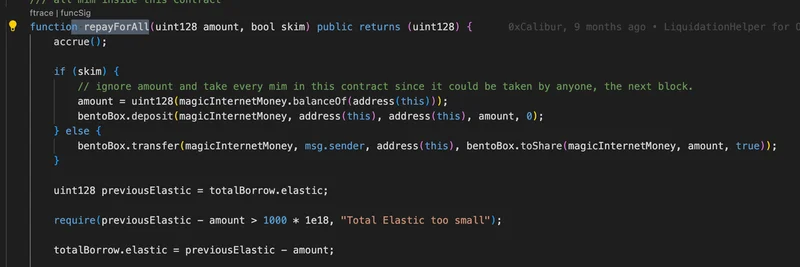
Abracadabra uses a shares system for debt tracking: Borrow shares stay fixed while assets grow with interest. The exploit abused repayForAll, which reduces total assets without shares, skewing ratios.
The attacker flash-loaned funds, repaid nearly all debts, then looped tiny borrows and repays to inflate total shares to near-infinity while keeping assets low. This let them borrow everything with minimal collateral, as the protocol misjudged their debt share.
Pure math wizardry—rounding up in the protocol's favor backfired in loops. Key fix: Ensure borrow shares can't drop below assets. Full thread here.
Raydium Critical Bugs: Tick and Liquidity Woes
Brainiac mentioned "Raydium 2 crit," likely referring to critical vulnerabilities in Raydium's CLMM, like the tick manipulation bug fixed in 2024.
In one, the increase_liquidity function let attackers manipulate ticks (price ranges) to add invalid liquidity, potentially draining pools. It involved math errors in position updates.
Raydium's code has explicit rounding directions to avoid value loss, but bugs in sqrt_price_math and liquidity_math can lead to exploits if not handled right.
For Solana-based meme tokens using Raydium, audit tick boundaries and math libs thoroughly.
Generic Rounding Horrors
TianCi_Club shared a classic: A rounding error draining an entire liquidity pool. These sneaky bugs often arise in fee calculations or share conversions, where flooring or ceiling accumulates losses over transactions.
In meme token land, where volatility amps up trades, such errors can evaporate funds fast. Always favor user-safe rounding and simulate extremes.
These exploits show how math bugs, often subtle rounding or precision slips, can unravel even well-audited protocols. As meme token hype surges, devs must prioritize security—consider audits from firms like Spearbit. Stay vigilant, and follow threads like this for real-world wisdom. What's your wildest bug story? Share in the comments!