Hey there, crypto enthusiasts! If you're deep into the world of meme tokens and blockchain tech, you've probably heard whispers about security threats lurking in the shadows. Well, renowned investigator ZachXBT just dropped a bombshell thread on X that peels back the curtain on how North Korean (DPRK) IT workers are sneaking into developer jobs using elaborate fake identities. This isn't just spy novel stuff—it's a real risk that could impact your favorite meme projects. Let's break it down step by step, with all the juicy details from Zach's expose.
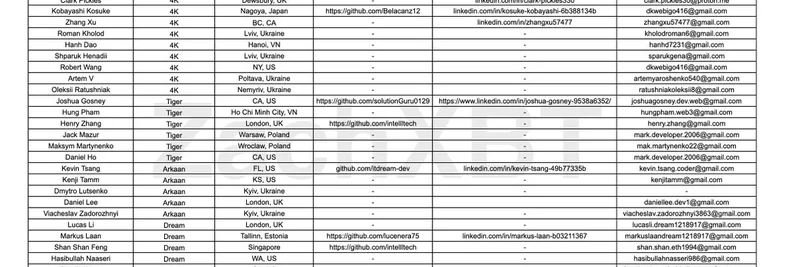
Zach starts off by sharing insights from a compromised device belonging to a small team of five DPRK IT workers. These folks were running over 30 fake identities, complete with government IDs, to snag jobs on platforms like Upwork and LinkedIn. They even bought accounts to make it all look legit. The goal? Infiltrate projects, potentially steal funds or intel, and funnel money back home.
One of the key revelations comes from an export of their Google Drive and Chrome profiles. These guys were super organized, using Google tools for schedules, tasks, and budgets—all in English. It's like peeking into a secret operation's playbook.
Moving on, Zach highlights a spreadsheet with weekly reports from 2025. It's eye-opening: team members admitting they don't understand job requirements but vowing to "put enough efforts in heart." Classic case of faking it till you make it, but with high stakes in crypto.
Expenses tell another story. These operatives were shelling out for SSNs (Social Security Numbers), Upwork and LinkedIn accounts, phone numbers, AI subscriptions, computer rentals, and VPNs/proxies. Everything needed to maintain the facade and stay under the radar.
Zach also shares a meeting schedule and a script for one fake identity, 'Henry Zhang.' They used AnyDesk for remote work on rented computers, making it hard to trace back to their real locations.
A wallet address pops up: 0x78e1a4781d184e7ce6a124dd96e765e2bea96f2c. This one's linked to payments and ties directly to the $680K Favrr exploit in June 2025, where the CTO and devs were DPRK plants with phony docs. More IT workers were spotted at other projects via this address.
Browser history and searches add more intrigue, showing queries that scream suspicious activity. And to answer the big question—"How do we know they're North Korean?"—frequent Google Translate to Korean, plus Russian IPs, and all those fraudulent docs seal the deal.
Zach wraps up by pointing out the challenges: lack of collaboration between services and the private sector, plus hiring teams getting defensive when warned. These IT workers aren't super sophisticated, but they're persistent, flooding the job market. Payoneer is a go-to for converting fiat to crypto from their gigs.
For anyone in the meme token scene, this is a wake-up call. When building or investing in projects, vet your devs thoroughly—check LinkedIn histories, run background checks, and watch for red flags like mismatched locations or generic profiles. Staying vigilant keeps the blockchain space safer for all of us.
If you're hungry for more on crypto security and meme token insights, stick around Meme Insider. We've got the latest scoops to help you navigate this wild world. What do you think about this expose? Drop your thoughts in the comments!