Hey folks, if you're knee-deep in the wild world of Solana meme tokens like the rest of us at Meme Insider, you've probably heard the buzz about this insane supply chain attack that just rocked the JavaScript ecosystem. We're talking about a hack on core NPM packages that could potentially siphon off your hard-earned crypto gains. Don't worry—I'm breaking it all down in plain English, no tech jargon overload, so you can stay safe while chasing those viral pumps.
A quick explainer: NPM is basically the go-to package manager for JavaScript developers. It's where coders grab ready-made libraries to build apps faster. Think of it as the App Store for code snippets. On September 8, 2025, attackers phished their way into a developer's NPM account and injected malware into 18 super-popular packages, including Chalk (for colorful console logs), strip-ansi, and debug. These bad boys rack up over 2 billion downloads a week—yep, that's a ton of exposure.
The malware? It's a sneaky crypto clipper. In simple terms, it swaps out your wallet addresses mid-transaction, so instead of sending tokens to your buddy (or yourself), they end up in the hacker's pocket. It even uses a smart algorithm called Levenshtein to make the fake addresses look almost identical to the real ones—super devious. This isn't some random virus; it's tailored for blockchain users, targeting Ethereum but potentially hitting Solana dApps too since many use JS frontends.
Why does this matter for meme token enthusiasts? Solana's ecosystem is booming with quick launches on platforms like Pump.fun, but a lot of those tools and wallets are built with JavaScript. If you're a dev deploying a new frog-themed token or just trading $BONK derivatives, your setup could be vulnerable. Imagine front-running your own meme coin launch because of tainted code—nightmare fuel.
From what we've seen in the thread by @StarPlatinumSOL, a respected voice in the Solana space, the attack started with a phishing email mimicking NPM support. The domain was fresh-registered, and boom—malicious updates went live fast. Devs spotted weird errors like "fetch is not defined" and dug into the obfuscated code (that's code hidden to dodge detection) revealing crypto-stealing functions.
No funds have been moved yet from the attacker's wallets (main one: 0xFc4a4858bafef54D1b1d7697bfb5c52F4c166976, plus backups like 0xa29eEfB3f21Dc8FA8bce065Db4f4354AA683c024), but that's cold comfort. The community jumped on it quick, thanks to alerts from folks like Ledger's CTO, but it highlights how one weak link can threaten billions in value.
So, how do you protect yourself and your meme token projects? Here's the no-BS advice straight from the thread and our experts at Meme Insider:
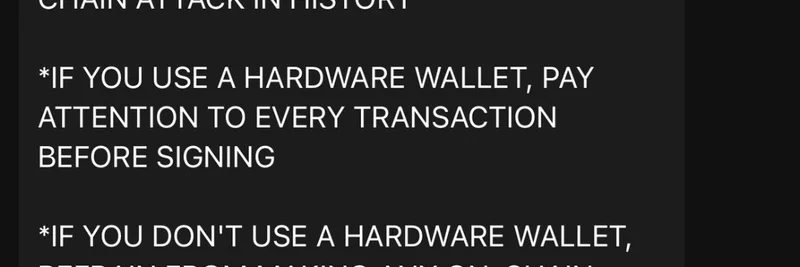
- Hardware Wallets Are Your Best Friend: If you're using a Ledger or Trezor, double-check every address before signing. The malware can't touch your keys if they're offline.
- Pin Your Packages: In your package.json file, lock in exact versions (e.g., "chalk": "5.3.0") to avoid auto-updating to bad versions.
- Use npm ci Over npm install: This installs exactly what's in your lockfile, skipping sneaky updates.
- Rotate Keys Now: Change your GitHub and NPM credentials ASAP. Phishing is the entry point here.
- For Solana Devs Specifically: Audit your frontend code if it handles wallet connections. Tools like Solana's own security guidelines can help. And if you're building meme launchers, consider Rust backends to minimize JS risks.
This incident is a wake-up call for the whole blockchain community, especially on fast-moving chains like Solana where meme tokens thrive on speed but can suffer from rushed security. At Meme Insider, we're all about empowering you with knowledge—stay vigilant, verify everything, and let's keep the meme magic alive without the hacks.
If you've been affected or spotted something fishy, drop a comment below or hit us up on meme-insider.com. For more on Solana security and the latest meme token drops, subscribe to our newsletter. Stay safe out there!