In the fast-paced world of crypto, where meme tokens and DeFi projects pop up like mushrooms after rain, security remains king. Recently, the team at BlockSec's Phalcon spotted some fishy activity on Ethereum involving the SIL token—a project created by DeFi pioneer Andre Cronje about four years ago. Attackers managed to siphon off around $120,000 by exploiting weaknesses in two unknown smart contracts. If you're into meme tokens or blockchain tech, this is a wake-up call on why proper safeguards matter.
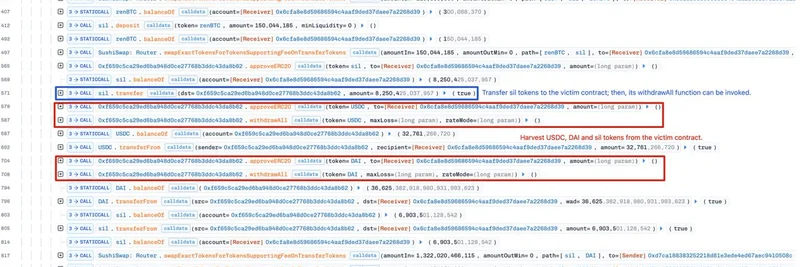
Let's break it down simply. The victim contracts—deployed by the same address but not open-sourced—had critical functions called approveERC20 and withdrawAll without any access controls. In plain English, access control is like a lock on your front door; without it, anyone can waltz in. Here, attackers could freely approve token transfers and withdraw assets stashed in these contracts, leading to the drainage.
The Attack Breakdown
The exploits unfolded across multiple transactions, each initiated by different externally owned accounts (EOAs)—that's just fancy talk for regular wallet addresses controlled by people or bots.
First Transaction: A Quick WBTC Grab
In the initial hit (view on Phalcon Explorer), the attacker targeted contract 0xd9d097b05862b73269e6eecd2e9912a815bbe7d6. They called approveERC20 to greenlight a transfer of Wrapped Bitcoin (WBTC), then used withdrawAll to pull out about 0.188 WBTC, worth roughly $21,000 at the time. Part of it was swapped via SushiSwap for ETH, and the rest funneled back to the attacker's wallet. Net loss here: around $37,000, mostly from a liquidity pool paired with SIL.
The Big One: Flashloan-Fueled Mayhem
The second transaction (view on Phalcon Explorer) was the heavy hitter, causing the bulk of the damage at about $109,000. What made this tricky? The withdrawAll function required burning a chunk of SIL tokens first—think of burning as permanently destroying tokens to meet a condition.
To get around this without owning SIL upfront, the attacker pulled off a flashloan from Balancer Vault. Flashloans are a DeFi superpower: you borrow massive amounts without collateral, but everything must be repaid in the same transaction, or it all reverts. Here, they borrowed 8 WETH and 115 USDT, then executed a series of swaps across platforms like Uniswap V3, SushiSwap, and Curve.fi to acquire enough SIL.
With SIL in hand, they burned the required amount, called the vulnerable functions on contract 0x6cfa8e8d59686594c4aaf9ded37daee7a2268d39, and drained a buffet of tokens: DAI, USDC, USDT, WBTC, MKR, SNX, LINK, YFI, AAVE, and more. The SIL token itself took the biggest hit, with liquidity pools losing over $69,000 worth. The attacker walked away with a mixed bag of assets, converting some to Ether for easy cash-out.
Phalcon mentioned a third transaction, but details are sparse—likely similar tactics with smaller gains to round out the $120K total.
Why SIL? And Is It a Meme Token?
SIL, or Silentium, isn't your typical dog-or-cat-themed meme coin, but it fits into the broader meme token ecosystem due to its community-driven vibes and liquidity on DEXes like SushiSwap. Created by Andre Cronje (the brains behind Yearn.finance), it started as an experimental token but has lingered in the shadows. This exploit underscores how even older, lesser-known tokens can become targets if linked to vulnerable contracts—especially in meme-heavy spaces where hype often outpaces security audits.
For context, SIL trades around $2.44 with low volume, per DEXTools data. Its involvement in impermanent loss protection on SushiSwap V2 might have made these pools juicy targets.
Lessons for Meme Token Enthusiasts
This isn't just another hack story; it's a reminder for blockchain practitioners. Meme tokens thrive on virality, but skimping on security can lead to disasters. Key takeaways:
- Audit Everything: Unverified contracts are red flags. Tools like Etherscan can help check code, but professional audits from firms like BlockSec are gold.
- Implement Access Controls: Use patterns like OpenZeppelin's Ownable to restrict who can call sensitive functions.
- Monitor for Suspicious Activity: Systems like Phalcon are lifesavers for spotting anomalies in real-time.
- Diversify and DYOR: If you're holding meme tokens, spread risks and research liquidity pools. Flashloan exploits are common in DeFi, so understand the protocols you're interacting with.
At Meme Insider, we're all about keeping you ahead in the meme token game. Stay tuned for more updates on exploits, tech news, and ways to level up your blockchain knowledge. If you've got thoughts on this SIL saga, drop them in the comments!
For more on Andre Cronje's projects, check out his X profile. And remember, in crypto, vigilance is your best meme.