In the fast-paced world of DeFi, security breaches can happen in the blink of an eye, and the recent attack on MIM Spell is a stark reminder of that. According to a detailed breakdown from blockchain security firm BlockSec's Phalcon team, the protocol suffered a loss of around $1.7 million due to a clever exploit in its core functionality. Let's break this down step by step, so even if you're new to smart contracts, you can follow along.
What Happened in the MIM Spell Attack?
The attack unfolded just hours ago, targeting the MIM Spell protocol—part of the Abracadabra ecosystem, which deals with stablecoins like MIM (Magic Internet Money). Attackers exploited a weakness in the "cook" function, a key feature that lets users bundle multiple operations into one transaction for efficiency. Think of it like a kitchen mixer: you throw in ingredients (actions) and get a cooked result. But in this case, the recipe had a fatal flaw.
By executing a specific sequence of actions—namely borrowing assets and then triggering a null operation—the hackers managed to sidestep crucial safety checks. This allowed them to borrow far more than they should have, walking away with about 1.793 million MIM tokens, which they quickly swapped for profits.
The Phalcon team spotlighted the exploit on X (formerly Twitter), highlighting how the shared status across actions created the vulnerability. It's a classic example of how even small oversights in code can lead to massive losses in the blockchain space.
Diving into the Root Cause
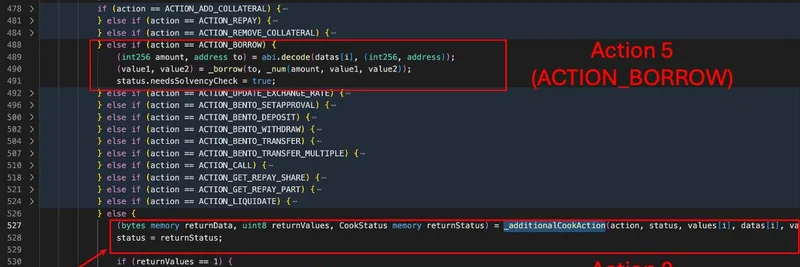
At the heart of the issue is the cook function's logic. Here's a simplified explanation:
Action 5 (BORROW): This is where the borrowing happens. When triggered, it sets a flag called
needsSolvencyCheckto true. This flag is supposed to ensure that after all operations, the user's account isn't underwater—meaning they don't owe more than their collateral covers.Action 0 (The Empty Trap): Following the borrow, the attacker slips in Action 0, which calls an internal function named
_additionalCookAction. But here's the kicker: this function is essentially empty. It does nothing and defaults to resetting theneedsSolvencyCheckflag to false.
Because all actions in the cook function share the same status object, this reset overwrites the earlier true flag. The result? The final insolvency check at the end of the transaction gets skipped entirely. No red flags raised, and the borrow goes through unchecked.
The attackers repeated this trick across six different addresses, using the action sequence [5, 0] each time. It's efficient, sneaky, and highlights why thorough auditing is non-negotiable in DeFi protocols.
Why This Matters for Meme Token Enthusiasts
While MIM itself is a stablecoin, the Abracadabra platform powers various meme-inspired and leveraged positions in the crypto world. Hacks like this ripple through the ecosystem, eroding trust and potentially impacting related tokens like SPELL. For meme token holders and traders, it's a wake-up call to diversify, use audited platforms, and stay informed about security alerts. After all, in the meme coin space, where hype drives value, a single exploit can turn gains into memes about losses.
If you're building or investing in blockchain projects, tools like Phalcon from BlockSec can help monitor threats in real-time. Staying vigilant is key—because as this incident shows, even established protocols aren't immune.
Lessons Learned and Moving Forward
This isn't the first rodeo for Abracadabra; similar issues have cropped up before, underscoring the need for robust, multi-layered security. Developers should prioritize isolated states for actions in batch functions and implement fail-safes that can't be bypassed so easily.
For the community, keep an eye on updates from MIM Spell and consider the risks before diving into any DeFi pool. Blockchain is exciting, but it's also a frontier where caution pays off. If you've been affected or have thoughts on this hack, drop a comment below—we'd love to hear your take.