In the fast-paced world of decentralized finance (DeFi), security incidents can strike without warning, and the recent attack on Yearn Finance's yETH stableswap pool is a stark reminder of that. Reported by blockchain security firm BlockSec's Phalcon team, this exploit led to losses estimated at around $9 million on the Ethereum network. If you're into crypto or meme tokens built on blockchain tech, understanding these vulnerabilities can help you navigate the space more safely.
Let's break it down step by step. Yearn Finance, a popular DeFi protocol, offers various tools for yield optimization, including stableswap pools. These are liquidity pools designed to minimize slippage for trades between similar assets, like different wrapped versions of ETH. The yETH pool specifically is a weighted stableswap that holds assets such as wstETH (wrapped staked ETH from Lido), rETH (Rocket Pool's staked ETH), cbETH (Coinbase's version), and mETH (from Mantle). The pool's LP token is yETH, which represents a share of the liquidity.
According to the original tweet from Phalcon, the attack unfolded in two main stages. It all started on November 30, 2025, at 21:11 UTC, as confirmed by Yearn's own announcement. The exploited contract was a custom version of a common stableswap code, separate from Yearn's other products like V2 or V3 vaults, so those weren't affected.
Stage 1: Draining the Pool's Supply to Zero
The attacker cleverly manipulated the pool to reduce its total supply of yETH—the token representing liquidity providers' shares—to zero. This involved a series of operations:
- Invoking the
update_rates()function, which seems to have consumed the original yETH supply in the pool. - Repeatedly adding and removing liquidity, combined with rate updates, to drive the effective supply down.
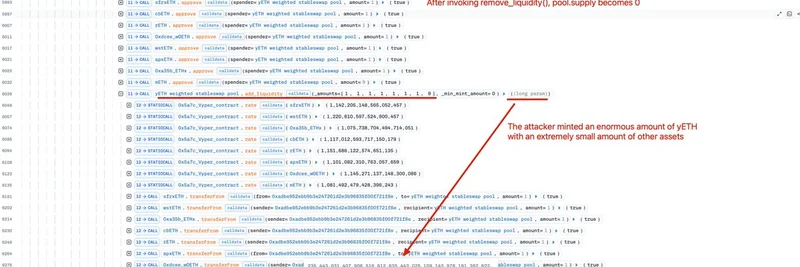
Once the supply hit zero, the pool was in a vulnerable state. Think of it like emptying a bank vault before rigging the system to print unlimited money. The Phalcon analysis highlights how the attacker called remove_liquidity() after these maneuvers, pushing the supply to absolute zero, as shown in this transaction breakdown:
Stage 2: The Infinite Mint and Profit Extraction
With the supply at zero, the attacker exploited a flaw allowing them to mint an absurdly large amount of yETH using tiny inputs. We're talking about minting over 235 quadrillion yETH (that's 235,443,031,407,908,519,912,635,443,025,109,143,978,181,362,622,575,235,916 to be precise) with just 1 wei of tokens like wstETH, rETH, cbETH, and 9 wei of mETH. Wei is the smallest unit of ETH, so this is essentially free.
Here's a visual from the transaction logs pointing to the minting step:
After minting this massive amount, the hacker swapped 100,000,000,000,000,000,000,000,000,000 yETH for about 1,079 ETH, pocketing the profits. The total loss to the pool was around $9 million, highlighting how even small flaws in smart contract logic can lead to huge exploits.
This incident echoes other recent DeFi hacks, where attackers target liquidity pools or token minting mechanisms. For meme token enthusiasts, it's a cautionary tale: many memes run on similar Ethereum-based protocols, and understanding DeFi basics like stableswaps can help spot risky projects.
Yearn Finance quickly acknowledged the issue, assuring users that core vaults remain safe. If you're holding yETH or involved in similar pools, it's wise to monitor updates from official sources like Yearn's Twitter or their docs.
Staying informed about these exploits not only protects your investments but also contributes to a more secure blockchain ecosystem. What do you think—will this lead to better auditing standards in DeFi? Share your thoughts in the comments!